Tips for Designing Security for Your Public APIs

[adsenseyu2] Before we look into tips & techniques to design security for your Public APIs, lets understand what do we mean by Public APIs? Public APIs are APIs that are published to the world including developers, or partners’ developers to create their custom application by making use of APIs. These APIs can be used by another program, mobile apps or web applications (Web UI), desktop client etc. Following are some tips/techniques for designing security for your Public APIs: IP Address Restrictions: To be able to control access to APIs based on IP address from which request arrived, the IP address restrictions policy should be imposed. This is very handy when …
List of Great Videos on API Design & Development
Following are some of the videos I could gather which presents talks on API design & development. How to Design a Good API and Why it Matters?: A great video by Joshua Bloch done some 6 years back. Great one for those looking to understand what API design & development look like and how to get started? How to Design Good APIs: This video focus on some of the key aspects such as intuitiveness, documentation of API. Life of a Google API Developer: This video presents different aspect of API development.
What makes an API, a great API?

[adsenseyu2] Before I start on this blog, lets take a look at the quote, “Being complex is easy, being simple is hard”. Do you agree? Well, I have experienced it and agree in totality. This is what it takes in creating a simple-to-understand-and-use API, a complex task. 🙂 Whenever I start writing about API, I do clarify what am I meaning for API? Most of the programmers would think if API is not same as interfaces to the classes that they write. Well, I would say that yes, they are same. However, we usually do not pay attention to write, what is called as “Great API”, as we write the …
A Great API should act as a Building Block!
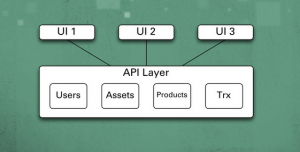
[adsenseyu2] Following are characteristics of a great API: Building Blocks: APIs consisting of one or more methods should act like building blocks that could be assembled in more than one unique ways to create newer applications or apps. This could thus lead to innovation where developers can take up these APIs and create some creative and unique applications serving different functionality and creating substantial value for the end users. For example, look at facebook apps or salesforce apps. Developers worldwide have created several innovative applications by using facebook APIs. Distinct & Stateless: APIs should be distinct in terms of its service offerings and stateless in nature. Thus, invocation of an …
List of Threat Modeling Tools
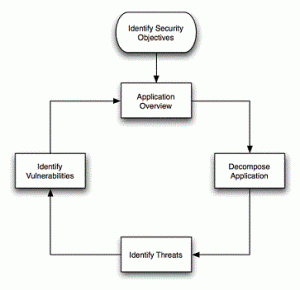
Threat modeling tools are used to perform systematic analysis of attack vectors by helping you analyze some of the following questions: Which are high-value assets? What does attacker profile may look like? Which are most vulnerable areas in the application which can be attacked by the hackers? What are most relevant threats to the application? Are there one or more attack vectors which can go unnoticed? Following is the list of top 5 threat modeling tools you may keep handy for threat modeling: Microsoft Free SDL Threat Modeling Tool: Tool from Microsoft that makes threat modeling easier for all developers by providing guidance on creating and analyzing threat models. Following diagram displays …
APIs is the Way to Go, You bet!
[adsenseyu2] Not sure if you are aware or not, but the world is waking up to keywords such as API-First, API-Driven Development (ADD) etc. And, this is creating confusion in application developers mind when they hear counter argument against their expression that they have always been doing API driven development where they use to write proper interfaces to their implementations. What is different from then to now? And, what do they need to do differently? But the more important thing to ask is what has led to everyone talking about API driven development? Following are some of the reasons (also, key technology trends of 2014) why APIs has been getting …
Top 4 Java Static Code Analysis Tools

[adsenseyu2] Before going over some of top static code analysis tools for Java, lets quickly look at why do we need static code analysis in the first place? Following are some of the reasons: Rules compliance: Pre-defined rules can be set as per the coding standard and automated static analysis could be run to figure out rules violation. This does cut down on the manual code review for the related rules. Code quality metrics: The static analysis could be used to measure some of the following based on which software code quality can be measured: Code complexity Unit test coverage Re-usability Duplication Reports: Creates management reports that can be used …
How to Debug PHP Code?

[adsenseyu2] If you have started on PHP programming and looking out for tips and techniques on how to debug PHP code, following may help you get started: var_dump command: var_dump command helps one to explore whats stored in arrays and objects. Following is the sample code: <?php $a = array(1, 2, array(“a”, “b”, “c”)); var_dump($a); ?> echo command: You could as well use the echo command to debug php program flow. <?php $foo = “foobar”; echo “foo is $foo”; ?> Configure Xdebug with Zend Studio or Eclipse PHP IDE: If you are tired of var_dump or echo commands, and write PHP code using IDE such as eclipe-php or Zend Studio, …
What does Agile Team Composition Look Like?

[adsenseyu2] If you are starting on new on agile methodology for application development, the question on what does agile team composition look like is a commonly asked one? The article presents the agile team composition for SCRUM development model. Given the fact that there will be multiple agile teams which may work towards release one or more products in an organization, following questions get tricky: Do we need one business analyst for each SCRUM team? How to deal with performance engineers? Should there be one in each team, or should there be centralized team? How to seal with security specialists? Again, should there be one security specialists for each team, or …
Some Source Code for Bonita Rest API Implementation

[adsenseyu2] Following are key source code blocks/classes/APIs to consider for you to get started with Bonita REST API implementation: AccessorUtil: This is the gateway API which is used to get instance of key API implementations. For example, AccessorUtil.getRuntimeAPI() gets you an instance of RuntimeAPI to work with. ProcessDefinitionUUID: The ProcessDefinitionUUID (org.ow2.bonita.facade.uuid.ProcessDefinitionUUID) class is one of the important parameter required to create an instance of process, such as ProcessInstanceUUID. Following code helps instantiate the process: ProcessDefinitionUUID processDefinitionUUID = new ProcessDefinitionUUID(process, version); try { return runtimeAPI.instantiateProcess(processDefinitionUUID, params); } catch (ProcessNotFoundException e) { } catch (VariableNotFoundException e) { } LightTaskInstance: LightTaskInstance (org.ow2.bonita.light.LightTaskInstance) defines the tasks for the workflow. RuntimeAPI: RuntimeAPI (org.ow2.bonita.facade.RuntimeAPI) is used to …
Bonita REST API & Application Architecture
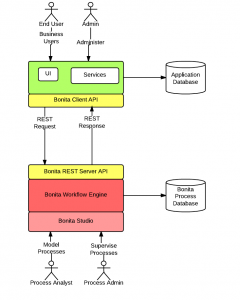
[adsenseyu2] I have been working on BonitaSoft REST API in order to meet following customers’ requirements: The customer has multiple line of business (LOB) applications. The customer has decided to make a strategic move to offer solutions to their existing and new customers rather than one or more products from their multiple LOBs which can be accessed by a web application dashboard. These solution span across multiple LOB applications and is envisioned to leverage functionality offered by these applications using service API. In this regard, one key fundamental architectural component that got introduced is workflow tool, BonitaSoft. The workflow tool is used to execute one or more workflows which forms …
Testing Early, Testing Often for Greater Success in Agile SCRUM

In my experiences, I have found two different approaches taken towards testing in Agile SCRUM: Testers creating test plans while interacting with BAs, as like in waterfall model, in the beginning of each sprint, and executing those tests once the development is done. In this model, testers and developers still managed to survive successfully in their own islands/worlds and things used to move. However, there is not much interaction and collaboration between developers and testers during development phase. There are chances of usual conflicts that happens in the world of development and testing. Testers creating test plans with help of BAs, collaborating on test cases, related with user stories, with …
My All-Time Web Application Security Favorites

Following are my all time favorites web pages I frequently visit for remaining up-to-date with web application security: https://www.owasp.org/ Website I frequently visit to check out videos, presentations, Books etc. http://bsimm.com/ Website about building security in maturity model http://www.webappsec.org/ Website representing Web Application Security Consortium that publishes technical information, contributed articles, security guidelines, and other useful documentation. Businesses, educational institutions, governments, application developers, security professionals, and software vendors all over the world utilize their materials to assist with the challenges presented by web application security. Books: List of web application security books you would want to keep handy Web Application Security Interview Questions: List of some interesting web security interesting …
My Bookmarks (03/12/2013)
Following are some of the links in the areas of APIs and mobile that I found interesting while reading: How to go about creating your APIs: The article presents write up on API design issues and the guidelines. Came across “Mobile-first” keyword Got started with creating tutorials on PHP Programming: The OOPs way on “Codecademy.com“. Considerations for choosing between mobile apps vs mobile websites.
Obamacare Website HealthCare.gov & Security Threats Review

Well, there have been lot of discussions around security issues with Obamacare website, healthcare.gov which has become talk of the town recently. The federal portal serves 36 states not operating their own health insurance exchanges. Fourteen other states and the District of Columbia run their own marketplaces. One of the factors attributing to security issues is sheer large volume of untested source code covering 500 millions lines of code. One of the most important security threat is related with information disclosure of the millions of Americans. The sensitive personal information of millions of Americans such as social security numbers (SSN), birthdays, incomes, home mortgages, and addresses is at risk. Another security …
Are Days Counted for MVC-based Web Applications?
Today, if I am tasked to lay down the architecture for web application, I would no longer be blindly choosing MVC based architecture. Additionally, if this is a migration project from legacy to web application, I would no longer be blindly going for MVC based architecture and choose related MVC frameworks. Not sure if you would agree with me or not. But please read the following and share your thoughts. I would be happy to hear from you. Why am I getting paranoid regarding MVC for web applications? Following are criteria for my considerations for deciding on whether I would select MVC architecture for delivering business functionality on the web: …

I found it very helpful. However the differences are not too understandable for me