This gallery contains 3 photos.
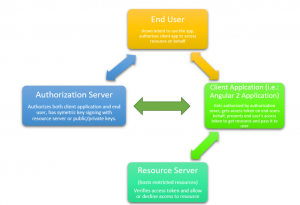
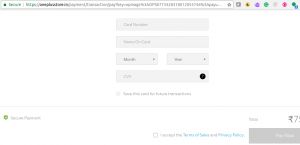
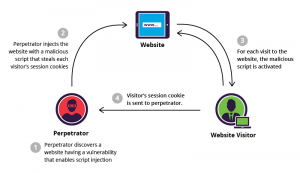
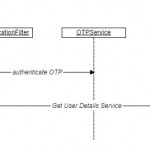
Why two factor authentication? With the increase in password theft, phishing attacks and other hacking techniques, the conventional text based user name and password based authentication seem to be insufficient because of the rapid rise of network level threats. The traditional way of just memorizing the password to validate one’s identity is not enough and web sites and applications are now expecting one to possess email Id or a smartphone to communicate with another short-lived randomized password, One Time Password (OTP), as one more factor to the authentication. Here we will discuss the approach to generate the OTP and use it for the two factor authentication technique. In the next …







I found it very helpful. However the differences are not too understandable for me