What to Learn on Day One of Application Development

Well, I would surely not recommend you to go over the application code and look for things like classes, interfaces, data model, design patterns etc. It definitely has to be everything else than the application code. If you have just landed on to a new application development project and shall be going to start working on the application soon, you may want to understand some of the following on day one rather than nitty-gritties of the application itself: Business overview: The idea is to understand key business functions which is served by the application. The output of business overview can be functional decomposition which can be later related to one …
Attention Developers: Take Care of Your Debts

Hmm.. was the title intriguing enough for you to check out if you as a developer got any debts to clear (such as that represented below :-)? Well, I am talking about what is called as “technical debt” and that is it. 🙂 Believe me, there are high possibilities that most of the developers do have technical debts to clear which they (or someone else) introduce in the system while working on it over a period of time. Lets try and understand what/how/why/whens related with technical debt? As Fowler writes in his blog, technical Debt is a wonderful metaphor developed by Ward Cunningham to help us think about this …
Tips for Newbies to Choose between Technologies

Does the above picture include one of the programming languages you are planning to learn or have started learning? I have come across many a newbies frequently looking for answers to some of the following questions: Which technology will be most suitable for me from career perspective? Which technology will help me secure high-paying job? Which technology will I love to work with? Is development (coding) good for me or, I could also explore testing career? Should I go on to learn one of the programming languages such as Java, C#, PHP, RoR etc, or should I learn one of the application packages such as that related with ecommerce (ATG, Hybris, …
Follow Single Responsibility Principle & You are Home!

Here is an interview with Ajitesh Shukla who has been very passionate about coding all these years and have helped many software developers to write better code by getting them understand few basic coding principles. Read on to find out about his experience and expertise around coding. Tell us something about yourself, in brief My name is Ajitesh Kumar and I have got an experience of around 14 years working in different technologies such as Java, PHP etc. I am currently working on projects related with software quality governance, BonitaSoft, enterprise architecture, ATG etc. Tell us about your coding experience, in brief. I have been coding in different languages including …
New Initiative – Geeks’ Brain’s Picks

We are starting on a new initiative to share the pick of software geeks’ brains. The objective is to share information about beliefs, experience & expertise of software geeks out there who have been doing some real cool stuff. We are reaching out to many of these geeks and getting ready to start publishing information about them very soon. What is there for everyone’s out there? If you are a fresher/newbie who want to learn the software coding best practices from the horses’ mouth or, a tech lead/project manager who want to make sure their team follows a consistent coding best practices, you may want to pay attention to one …
Tips for Gathering Security Requirements of your Web Application Project

Gathering security requirements in relation with a project, sprint (if agile) is key to deliver secured applications. This is because security requirements would lead to appropriate design in relation with security. Following are key topics to consider for gathering security requirements: Authentication & password management: This is mostly a one-time activity and done as the start of the project and not in every sprint. One may want to ask questions such as following in relation with authentication and password management: Password policies: This is important to ask to avoid dictionary attack in relation with user credentials. Password hashing: This is important to make sure password is encrypted with appropriate encryption …
Atlassian Confluence-JIRA Integration to Strengthen Agile Portfolio

Earlier this week, Enterprise software toolmaker Atlassian announced tighter integration between its JIRA issue tracking application and its Confluence team collaboration platform. With this move, they have further strengthened their agile portfolio. Following is the list of software in their agile portfolio: Confluence: Confluence pages are used to maintain requirements (stories), technical specs, design guidelines, etc. Confluence pages are linked with JIRA thus linking requirements/technical specs to stories. JIRA: JIRA is used to maintain epics/stories and issues. There are several blueprints in JIRA created to manage status reports, retrospective meetings etc. The new JIRA Report Blueprint allows development teams to create an ad-hoc status report or a change log in Confluence. The new Retrospective Blueprint gives scrum masters, …
Top 7 Security Attack Questions While Analyzing Every Requirement

Following are top 5 security attack related questions that you could ask while analyzing the each requirement in hand, the answers to which could help you put better design in relation with security: Security threats analysis related with data entering into/coming out of the system: How could an attacker inject SQL commands? (OWASP SQL Injection). Solution: Use parameterized SQL queries rather than building SQL statements dynamically using string concatenation How could an attacker perform a cross-site scripting attack? (OWASP Cross-Site Scripting – XSS). Solution: Use OWASP ESAPI to sanitize user input against scripts such as Javascript that could lead to XSS attacks. This is more about doing input data validation as soon as …
Tips for Designing Security for Your Public APIs

[adsenseyu2] Before we look into tips & techniques to design security for your Public APIs, lets understand what do we mean by Public APIs? Public APIs are APIs that are published to the world including developers, or partners’ developers to create their custom application by making use of APIs. These APIs can be used by another program, mobile apps or web applications (Web UI), desktop client etc. Following are some tips/techniques for designing security for your Public APIs: IP Address Restrictions: To be able to control access to APIs based on IP address from which request arrived, the IP address restrictions policy should be imposed. This is very handy when …
List of Great Videos on API Design & Development
Following are some of the videos I could gather which presents talks on API design & development. How to Design a Good API and Why it Matters?: A great video by Joshua Bloch done some 6 years back. Great one for those looking to understand what API design & development look like and how to get started? How to Design Good APIs: This video focus on some of the key aspects such as intuitiveness, documentation of API. Life of a Google API Developer: This video presents different aspect of API development.
What makes an API, a great API?

[adsenseyu2] Before I start on this blog, lets take a look at the quote, “Being complex is easy, being simple is hard”. Do you agree? Well, I have experienced it and agree in totality. This is what it takes in creating a simple-to-understand-and-use API, a complex task. 🙂 Whenever I start writing about API, I do clarify what am I meaning for API? Most of the programmers would think if API is not same as interfaces to the classes that they write. Well, I would say that yes, they are same. However, we usually do not pay attention to write, what is called as “Great API”, as we write the …
A Great API should act as a Building Block!
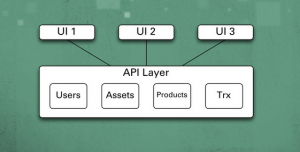
[adsenseyu2] Following are characteristics of a great API: Building Blocks: APIs consisting of one or more methods should act like building blocks that could be assembled in more than one unique ways to create newer applications or apps. This could thus lead to innovation where developers can take up these APIs and create some creative and unique applications serving different functionality and creating substantial value for the end users. For example, look at facebook apps or salesforce apps. Developers worldwide have created several innovative applications by using facebook APIs. Distinct & Stateless: APIs should be distinct in terms of its service offerings and stateless in nature. Thus, invocation of an …
List of Threat Modeling Tools
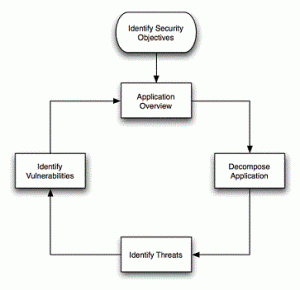
Threat modeling tools are used to perform systematic analysis of attack vectors by helping you analyze some of the following questions: Which are high-value assets? What does attacker profile may look like? Which are most vulnerable areas in the application which can be attacked by the hackers? What are most relevant threats to the application? Are there one or more attack vectors which can go unnoticed? Following is the list of top 5 threat modeling tools you may keep handy for threat modeling: Microsoft Free SDL Threat Modeling Tool: Tool from Microsoft that makes threat modeling easier for all developers by providing guidance on creating and analyzing threat models. Following diagram displays …
APIs is the Way to Go, You bet!
[adsenseyu2] Not sure if you are aware or not, but the world is waking up to keywords such as API-First, API-Driven Development (ADD) etc. And, this is creating confusion in application developers mind when they hear counter argument against their expression that they have always been doing API driven development where they use to write proper interfaces to their implementations. What is different from then to now? And, what do they need to do differently? But the more important thing to ask is what has led to everyone talking about API driven development? Following are some of the reasons (also, key technology trends of 2014) why APIs has been getting …
Top 4 Java Static Code Analysis Tools

[adsenseyu2] Before going over some of top static code analysis tools for Java, lets quickly look at why do we need static code analysis in the first place? Following are some of the reasons: Rules compliance: Pre-defined rules can be set as per the coding standard and automated static analysis could be run to figure out rules violation. This does cut down on the manual code review for the related rules. Code quality metrics: The static analysis could be used to measure some of the following based on which software code quality can be measured: Code complexity Unit test coverage Re-usability Duplication Reports: Creates management reports that can be used …
How to Debug PHP Code?

[adsenseyu2] If you have started on PHP programming and looking out for tips and techniques on how to debug PHP code, following may help you get started: var_dump command: var_dump command helps one to explore whats stored in arrays and objects. Following is the sample code: <?php $a = array(1, 2, array(“a”, “b”, “c”)); var_dump($a); ?> echo command: You could as well use the echo command to debug php program flow. <?php $foo = “foobar”; echo “foo is $foo”; ?> Configure Xdebug with Zend Studio or Eclipse PHP IDE: If you are tired of var_dump or echo commands, and write PHP code using IDE such as eclipe-php or Zend Studio, …
I found it very helpful. However the differences are not too understandable for me