AWS reInvent – Top 7 New Machine Learning Services
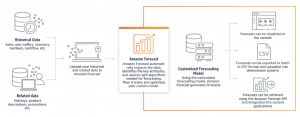
In this post, you will learn about some great new and updated machine learning services which have been launched at AWS re:Invent Conference Nov 2018. My personal favorite is Amazon Textract. Amazon Personalize Amazon Forecast Amazon Textract Amazon DeepRacer Amazon Elastic inference AWS Inferentia Updated Amazon Sagemaker Amazon Personalize for Personalized Recommendations Amazon Personalize is a managed machine learning service by Amazon with the primary goal to democratize recommendation system benefitting smaller and larger companies to quickly get up and running with the recommendation system thereby creating the great user experience. Here is the link to Amazon Personalize Developer Guide. The following are some of the highlights: Helps personalize the user experience using some of …
Solution – Macbook Air Stuck at Progress Bar Loading

In this post, you will learn about the solution related to Mac Air Stuck at Progress Bar Loading. The reason I am doing this post is that my Mac Air had been showing the same behavior for the last several months and I was able to finally fix it. I am hoping that the solution does help someone. Anyways, in the whole process, I started my Mac Air several times in voice-over mode and became expert at it. Commands/Solutions which didn’t work I contacted Apple customer service two times and they said that it looks to be a software problem after I tried all the steps they suggested. I was asked to …
Guidelines for Creating an Ethical AI Framework
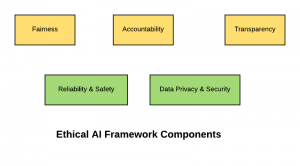
In this post, you will learn about how to create an Ethical AI Framework which could be used in your organization. In case, you are looking for Ethical AI RAG Matrix created with Excel, please drop me a message. The following are key aspects of ethical AI which should be considered for creating the framework: Fairness Accountability Transparency Reliability & Safety Data privacy and security Fairness AI/ML-powered solutions should be designed, developed and used in respect of fundamental human rights and in accordance with the fairness principle. The model design considerations should include the impact on not only the individuals but also the collective impact on groups and on society at large. The following represents some …
GitFlow Workflow Best Practices & Quiz Questions
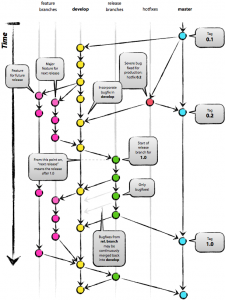
In this post, you will learn about some of the best practices in relation to managing your development and production releases using GitFlow Workflow. There will be a master branch which is called as an official repository. Forking a develop branch of the master: To start with, we will fork off another branch of the master which we may call as “develop”. This branch will act as an integration branch for features branches. NOTE: feature in features branches does not represent the features in machine learning. “Develop” branch will act as a parent to the feature branches. This means that developers would fork from “develop” branch and their changes are merged back into “develop” branch. In real-world scenarios, …
Javascript Security Vulnerabilities Examples (DarwinBox)
In this post, you will learn quick tips on security vulnerabilities related to Javascript based on analysis of how Javascript assets are managed in DarwinBox, and how to fix those security vulnerabilities. Security Vulnerabilities found with Javascript Assets While assessing the Javascript assets of DarwinBox, the following was found: Coding: Javascript code could be easily read and understood. There is a need to minimize and uglify the code. Method naming: The name of methods leak the implementation details and the underlying technology used. This could be used by hackers for planning attacks. For example, the method such as “doElasticSearch”. This represents that ElasticSearch is used for the search. File naming: The name of files represented …
Angular Bootstrap Hello World App – Sample Code
In this post, you will learn about how to get your Angular App to use Bootstrap CSS and Javascript libraries for creating some great UI. The following are the steps for creating the Angular app with Bootstrap CSS and Javascript: Get started by creating a Hello World App. Check out the post, Angular 7 Hello World App for greater details. Go to the folder consisting of index.html. This is the folder src within the project folder. Place the following code within the head tag. The code primarily represents the Bootstrap CSS file and a viewport meta tag for responsive pages. Place the following code within the body tag. The code represents Javascript libraries of JQuery and Bootstrap. Test the Angular …
Ethical AI Principles – IBM, Google, Intel, Microsoft
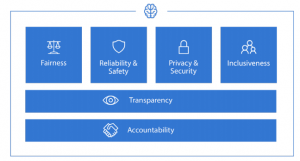
In this post, you will get a quick glimpse of ethical AI principles of companies such as IBM, Intel, Google, and Microsoft. The following represents the ethical AI principles of companies mentioned above: IBM Ethical AI Principles: The following represents six ethical AI principles of IBM: Accountability: AI designers and developers are responsible for considering AI design, development, decision processes, and outcomes. Value alignment: AI should be designed to align with the norms and values of your user group in mind. Explainability: AI should be designed for humans to easily perceive, detect, and understand its decision process, and the predictions/recommendations. This is also, at times, referred to as interpretability of AI. Simply …
IEEE Bookmarks on Ethical AI Considerations

In this post, you will get to have bookmarks for ethical AI by IEEE (Institute of Electrical and Electronics Engineers) group. Those starting on the journey of ethical AI would find these bookmarks very useful. ML researchers and data scientists would also want to learn about ethical AI practices to apply them while building and testing the models. The following are some bookmarks on ethical AI considerations by IEEE group: The IEEE Global Initiative on Ethics of Autonomous and Intelligent Systems: An initiative by IEEE for setting up new standards and solutions, certifications and codes of conduct, and consensus building for ethical implementation of intelligent technologies to ensure that these technologies are …
AI-powered Project Baseline to Map Human Health

In this post, you will learn about technologies and data gathering strategy for Project Baseline, an initiative by Google. Project Baseline is an IOT-based AI-powered initiative to map human health. Different kinds of machine learning algorithms including deep learning etc would be used to understand different aspects of human health and make predictions for overall health improvements and precautionary measures. This would require a very large volume of data to be gathered and processed before being fed into AI models. The following represents the data gathering strategies for Project Baseline: Diagnostic tests covering blood-related tests; specialized tests such as ECG, chest X-ray, eyesight check Doctor examination leading to the collection of data related to health …
Machine Learning Models – Bias Mitigation Strategies
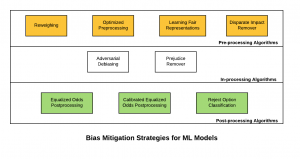
In this post, you will learn about some of the bias mitigation strategies which could be applied in ML Model Development lifecycle (MDLC) to achieve discrimination-aware machine learning models. The primary objective is to achieve a higher accuracy model while ensuring that the models are lesser discriminant in relation to sensitive/protected attributes. In simple words, the output of the classifier should not correlate with protected or sensitive attributes. Building such ML models becomes the multi-objective optimization problem. The quality of the classifier is measured by its accuracy and the discrimination it makes on the basis of sensitive attributes; the more accurate, the better, and the less discriminant (based on sensitive attributes), the better. The following are some of …
Facebook Machine Learning Tool to Check Terrorists Posts
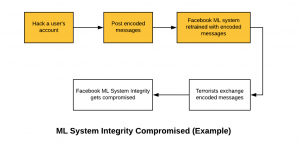
In this post, you will learn about details on Facebook machine learning tool to contain online terrorists propaganda. The following topics are discussed in this post: High-level design of Facebook machine learning solution for blocking inappropriate posts Threat model (attack vector) on Facebook ML-powered solution ML Solution Design for Blocking Inappropriate Posts The following is the workflow Facebook uses for handling inappropriate messages posted by terrorist organizations/users. Train/Test a text classification ML/DL model to flag the posts as inappropriate if the posts is found to contain words representing terrorist propaganda. In production, block the messages which the model could predict as inappropriate with very high confidence. Flag the messages for data analysts processing if the …
DevOps Maturity Model – Telstra DevOps Implementation
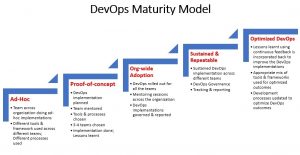
In this post, you will get a quick glimpse of how Telstra successfully rolled out DevOps across the entire organization (170 teams). The details have been taken from this post. You could use the details given below to lay out the maturity model for DevOps implementation in your organization. The following is the DevOps Maturity Model which Telstra team looks to have worked upon: Here are the key aspects of the DevOps practice (implementation) vis-a-vis maturity model: Ad-hoc implementations Teams across the organization doing ad-hoc implementations Different tools & framework used across different teams Different processes followed Teams do not seem to have a proper understanding of what is DevOps, benefits of DevOps etc. Proof-of-concept …
Angular – Firebase Authentication using Email Password
In this post, you will learn about angular code sample or example related to firebase authentication using email and password in an Angular app. The code has been tested with Angular 7.* and latest version of AngularFire. You will learn some of the following in this post: Login code example using Firebase Method, signInWithEmailAndPassword LoginComponent code for invoking Firebase Authentication using AuthService Login Code Example using Firebase Method, signInWithEmailAndPassword The code could be put inside a file such as auth.service.ts. Pay attention to the fact that an instance of Observable is returned from the login api. In the above code, a GenericResponse object is used for capturing the error message details. The following represents the code for GenericResponse object. …
ML Model Fairness Research from IBM, Google & Others
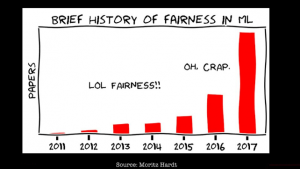
In this post, you would learn about details (brief information and related URLs) on some of the research work done on AI/machine learning model ethics & fairness (bias) in companies such as Google, IBM, Microsoft, and others. This post will be updated from time-to-time covering latest projects/research work happening in various companies. You may want to bookmark the page for checking out the latest details. Before we go ahead, it may be worth visualizing a great deal of research happening in the field of machine learning model fairness represented using the cartoon below, which is taken from the course CS 294: Fairness in Machine Learning course taught at UC Berkley. IBM Research for ML Model Fairness …
Angular 7 Hello World App – Instructions
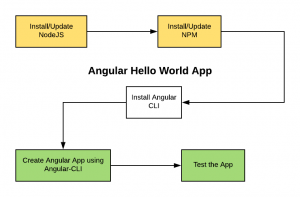
In this post, you would learn about how to quickly get started with Angular 7 hello world app. Here are the steps to build the Angular App. Actually, the steps could be used to build an Angular app with any version of Angular such as Angular 6 or Angular 5. Install NodeJS: Install the NodeJS. Angular requires Node.js version 8.x or 10.x. If you already have Node installed, check the version using the command, node -v and update the NodeJS to latest version appropriately using instructions provided on this page, How to update NodeJS and NPM to next versions. In case you do not have NodeJs installed, go to NodeJS website and download the appropriate NodeJS version. Install …
Fairness Metrics – ML Model Sensitivity for Bias Detection
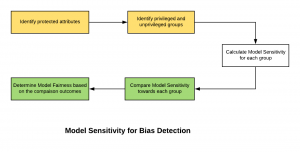
There are many different ways in which machine learning (ML) models’ fairness could be determined. Some of them are statistical parity, the relative significance of features, model sensitivity etc. In this post, you would learn about how model sensitivity could be used to determine model fairness or bias of model towards the privileged or unprivileged group. The following are some of the topics covered in this post: How could Model Sensitivity be used to determine Model Bias or Fairness? Example – Model Sensitivity & Bias Detection How could Model Sensitivity determine Model Bias or Fairness? Model sensitivity could be used as a fairness metrics to measure the model bias towards the privileged or unprivileged group. Higher the …

I found it very helpful. However the differences are not too understandable for me