Category Archives: Database
CEP vs Traditional Database Examples
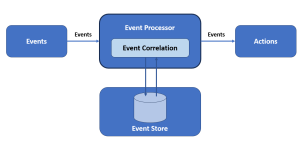
In this blog, we will learn about the differences between complex event processing (CEP) and traditional database querying with the help of examples. We will learn about how these two methodologies tackle data to extract meaningful insights but in fundamentally different ways. In complex event processing, data flows dynamically which is then matched with pre-defined patterns thereby generating insights in real-time. Traditional Database Querying In a conventional database querying scenario, the data is stored first, and then queries are run against this stored data to find patterns or retrieve information. This process is reactive, in that the query is formulated based on a need to find out something specific about …
Types of SQL Joins: Differences, SQL Code Examples
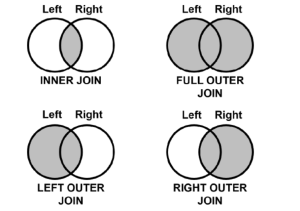
Structured Query Language (SQL) is one of the most important and widely used tools for data manipulation. It allows users to interact with databases, query and manipulate data, and create reports. One of SQL’s most important features is its ability to join tables together in order to enrich, compare and analyze related data. These joins are termed as inner join, outer join, left join and right join. In this article, we will discuss the different types of joins available in SQL, their differences and provide examples of how each can be used. What is SQL Join? SQL Joins are a technique used in Structured Query Language (SQL) to combine two …
NoSQL Data Models Types: Concepts & Examples
Not every data set fits neatly into a traditional SQL relational database. To address the need for more flexible databases, NoSQL data models were developed. These models allow for faster development cycles, larger data sets and greater scalability than traditional SQL databases. In this post, we’ll provide an overview of NoSQL data models and some examples of how they are used in real-world applications. NoSQL Data Model Types NoSQL data models can be divided into four main types: document stores, key-value stores, graph databases, and column stores. Each type has its own unique strengths and weaknesses and is best suited to certain types of applications or use cases. Here’s a …
Scaling Techniques for Relational Databases
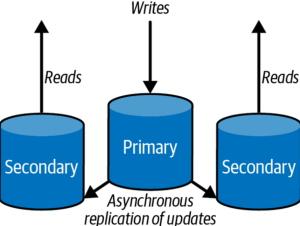
When it comes to relational databases, scaling can be a difficult process. As data volume increases, the performance of the database can suffer. To ensure that your database continues to perform at its best, you must scale it properly. In this blog post, we’ll explore some of the techniques used to scaling up and scaling out the relational databases for maximum performance. Scaling up Scaling up (vertical scaling) of a relational database is the practice of increasing the capacity of a single server, either by adding more memory, processors, and/or storage to the existing setup. As a matter of fact, this technique can also be used for non-relational databases. This …
NoSQL Databases List & Examples
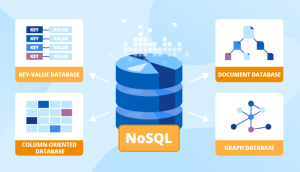
With the proliferation of big data, there has been a corresponding increase in the number of NoSQL databases. For those who are new to the term, NoSQL databases are non-relational databases that are designed to handle large amounts of data. In this blog post, we will take a look at some of the most popular NoSQL databases. NoSQL databases are a newer alternative to traditional relational databases that are designed to provide more flexibility and scalability. NoSQL databases are often used for big data applications that require real-time analysis or for applications that need to be able to handle a large amount of concurrent users. While NoSQL databases can offer …
AWS Error 2003 – Can’t Connect to RDS MySQL Server
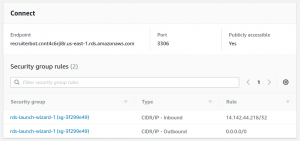
In this post, you will learn about the solution to the error, AWS Error 2003: Can’t Connect to RDS MySQL Server, which you may come across while trying to connect AWS MySQL RDS server from your local machine (laptop or desktop). I came across this error when I first created an RDS MySQL instance using AWS console and tried accessing the instance from my laptop using the command such as mysql -h endpoint_address -P 3306 -u username -p. The following represents the error: As a matter of fact, I have come across this error once in a while trying to connect the MySQL database app from the command prompt or the application. The solution works …
DynamoDB – Partition Key vs Composite Partition Key

AWS DynamoDB has two key concepts related to table design or creating new table. A beginner with DynamoDB is found to be wondering on whether to use a partition key or composite partition key when creating a new table. Composite partition key is also termed as composite primary key or hash-range key. In this post, you will learn about some of the following: Is the partition key same as the primary key of a table? What are composite partition key or composite primary key? When to use partition key vs composite partition key? This post presumes that you have got a good understanding of partition concept and how DynamoDB stores …
Consistent Hashing Concepts – Databases, DHT
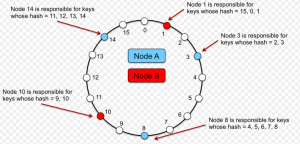
This blog represents What’s The Funda (WTF) around consistent hashing and DHT (Distributed Hash Tables), Databases use cases where it is used. Problems with Traditional Hashing Mechanism Lets understand the traditional hashing mechanism using following diagram: Pay attention to some of the following aspects as per the above diagram: Hash table/map is an array with each of the array index pointing to a linked list having each node representing a key-value pair. Keys are passed through a hash function. The index of the array (bucket) to which a specific key-value pair would get associated is a function of hash value and total size of the array. For example, in above diagram, key such as “Sam …
Dummies Notes – How to Setup Oracle Data Guard
This article represents instructions which could be used to set up oracle data guard on a primary and one or more physical standby database. The article presumes that you have a basic understanding of what is Oracle Data guard and why it needs to be set up. Following are key aspects which are discussed later in this article: Primary Database Setup Physical Standby Database Setup Following is details on primary and physical standby database setup: Primary Database Setup: Configure the primary database appropriately including doing some of the following: Enable force logging Alter the database parameters such as following. This is one time activity and does not needed to be …

I found it very helpful. However the differences are not too understandable for me