In this blog, we will learn about the differences between complex event processing (CEP) and traditional database querying with the help of examples. We will learn about how these two methodologies tackle data to extract meaningful insights but in fundamentally different ways. In complex event processing, data flows dynamically which is then matched with pre-defined patterns thereby generating insights in real-time.
Traditional Database Querying
In a conventional database querying scenario, the data is stored first, and then queries are run against this stored data to find patterns or retrieve information. This process is reactive, in that the query is formulated based on a need to find out something specific about the data that has already been collected. The database waits passively for queries, and the patterns or insights to be discovered are not defined until someone decides to look for them.
Complex Event Processing (CEP)
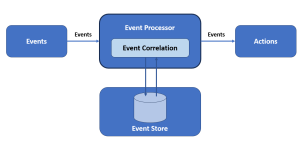
CEP flips this traditional model on its head. Instead of storing data and then querying it, CEP involves defining the patterns or conditions of interest upfront, before any data is received. These patterns are specified in the CEP engine, a specialized processing system designed to handle high-velocity data streams. Unlike traditional data analysis, where data is stored and then queries are run to find patterns, CEP works by continuously analyzing live data streams to detect these patterns as the data flows in. The following represents the CEP architecture.
The key advantage of CEP is its ability to provide immediate insights and responses to patterns in data as they occur, without the latency inherent in storing and then querying data. This makes CEP particularly valuable in scenarios where timeliness is critical, such as fraud detection, real-time monitoring, and instant decision-making applications.
Let’s understand how CEP works by considering an example of credit card fraud detection:
- Pattern Definition: In CEP, you start by specifying a “pattern” or a set of criteria that you’re interested in. This could be something like detecting fraudulent transactions in a financial system, identifying unusual patterns in sensor data that might indicate a malfunction, or spotting specific trends in social media posts. In the context of credit card fraud detection, a bank might define a pattern that indicates potential fraud. This could be something like “multiple transactions occurring in different countries within a short time frame” or “a sudden high-value purchase far from the cardholder’s usual location.”
- Streaming Data: Instead of dealing with static, stored data, CEP operates on live, streaming data. This data represents a continuous flow of events, such as financial transactions, sensor readings, or social media updates. In the context of credit card fraud detection, every transaction made with a credit card generates a stream of data that includes information like the transaction amount, location, time, and merchant details. This data is continuously flowing into the bank’s system in real-time.
- Real-Time Analysis: As the stream of events enters the CEP system, the engine continuously analyzes this incoming data in real time, looking for occurrences that match the predefined patterns. In the context of credit card fraud detection, the bank’s CEP system is configured with predefined fraud detection patterns. As each transaction data point streams in, the CEP engine immediately analyzes it against these patterns. It’s like the system is constantly asking, “Does this transaction fit any of the fraud patterns I’m looking for?”
- Event Matching and Emission: When the CEP engine identifies events in the data stream that fit the specified pattern, it recognizes these as “complex events.” These complex events are then emitted as a new stream of data, which can be used to trigger actions, send alerts, or further analysis. In the context of credit card fraud detection, when the CEP system identifies a transaction that matches one of the fraud patterns, it flags it as a potential fraud event—a “complex event.” The system can then automatically trigger a response, such as blocking the transaction, alerting the cardholder, or flagging the account for further review.
- Completion Model vs Chat Model: Python Examples - June 30, 2024
- LLM Hosting Strategy, Options & Cost: Examples - June 30, 2024
- Application Architecture for LLM Applications: Examples - June 25, 2024
Leave a Reply