Author Archives: Ajitesh Kumar
Python – How to install mlxtend in Anaconda
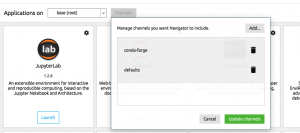
In this post, you will quickly learn about how to install mlxtend python package while you are working with Anaconda Jupyter Notebook. Mlxtend (machine learning extensions) is a Python library of useful tools for the day-to-day data science tasks. This library is created by Dr. Sebastian Raschka, an Assistant Professor of Statistics at the University of Wisconsin-Madison focusing on deep learning and machine learning research. Here is the instruction for installing within your Anaconda. Add a channel namely conda-forge by clicking on Channels button and then Add button. Open a command prompt and execute the following command: conda install mlxtend –channel Conda-forge Once installed, launch a Jupyter Notebook and try importing the following. This should work …
Python DataFrame – Assign New Labels to Columns
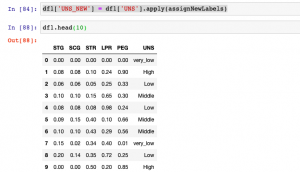
In this post, you will get a code sample related to how to assign new labels to columns in python programming while training machine learning models. This is going to be very helpful when working with classification machine learning problem. Many a time the labels for response or dependent variable are in text format and all one wants is to assign a number such as 0, 1, 2 etc instead of text labels. Beginner-level data scientists will find this code very handy. We will look at the code for the dataset as represented in the diagram below: In the above code, you will see that class labels are named as very_low, Low, High, Middle …
Java Implementation for Rosenblatt Perceptron
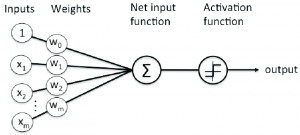
In this post, you will learn about Java implementation for Rosenblatt Perceptron. Rosenblatt Perceptron is the most simplistic implementation of neural network. It is also called as single-layer neural network. The following diagram represents the Rosenblatt Perceptron: The following represents key aspect of the implementation which is described in this post: Method for calculating “Net Input“ Activation function as unit step function Prediction method Fitting the model Calculating the training & test error Method for calculating “Net Input” Net input is weighted sum of input features. The following represents the mathematical formula: $$Z = {w_0}{x_0} + {w_1}{x_1} + {w_2}{x_2} + … + {w_n}{x_n}$$ In the above equation, w0, w1, w2, …
Difference between Adaline and Logistic Regression
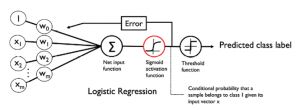
In this post, you will understand the key differences between Adaline (Adaptive Linear Neuron) and Logistic Regression. Activation function Cost function Difference in Activation Function The primary difference is the activation function. In Adaline, the activation function is called as linear activation function while in logistic regression, the activation function is called as sigmoid activation function. The diagram below represents the activation functions for Adaline. The activation function for Adaline, also called as linear activation function, is the identity function which can be represented as the following: $$\phi(W^TX) = W^TX$$ The diagram below represents the activation functions for Logistic Regression. The activation function for Logistic Regression, also called as sigmoid activation function, is …
Logistic Regression: Sigmoid Function Python Code
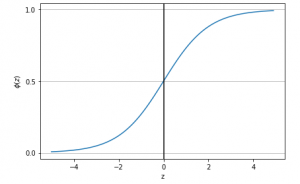
In this post, you will learn about the following: How to represent the probability that an event will take place with the asssociated features (attributes / independent features) Sigmoid function python code Probability as Sigmoid Function The below is the Logit Function code representing association between the probability that an event will occur and independent features. $$Logit Function = \log(\frac{P}{(1-P)}) = {w_0} + {w_1}{x_1} + {w_2}{x_2} + …. + {w_n}{x_n}$$ $$Logit Function = \log(\frac{P}{(1-P)}) = W^TX$$ $$P = \frac{1}{1 + e^-W^TX}$$ The above equation can be called as sigmoid function. Python Code for Sigmoid Function Executing the above code would result in the following plot: Pay attention to some of the …
Three Key Challenges of Machine Learning Models
In this post, you will learn about the three most important challenges or guiding principles that could be used while you are building machine learning models. The three key challenges which could be adopted while training machine learning models are following: The conflict between simplicity and accuracy Dimensionality – Curse or Blessing? The multiplicity of good models The Conflict between Simplicity and Accuracy Before starting on working for training one or more machine learning models, one would need to decide whether one would like to go for simple model or one would want to focus on model accuracy. The simplicity of models could be achieved by using algorithms which help …
Hypergeometric Distribution Explained with 10+ Examples
In this post, we will learn Hypergeometric distribution with 10+ examples. The following topics will be covered in this post: What is Hypergeometric Distribution? 10+ Examples of Hypergeometric Distribution If you are an aspiring data scientist looking forward to learning/understand the binomial distribution in a better manner, this post might be very helpful. The Binomial distribution can be considered as a very good approximation of the hypergeometric distribution as long as the sample consists of 5% or less of the population. One would need a good understanding of binomial distribution in order to understand the hypergeometric distribution in a great manner. I would recommend you take a look at some of my related posts on …
Binomial Distribution with Python Code Examples
In this code, you will learn code examples, written with Python Numpy package, related to the binomial distribution. You may want to check out the post, Binomial Distribution explained with 10+ examples to get an understanding of Binomial distribution with the help of several examples. All of the examples could be tried with code samples given in this post. Here are the instructions: Load the Numpy package: First and foremost, load the Numpy and Seaborn library Code Syntax – np.random.binomial(n, p, size=1): The code np.random.binomial(n, p, size=1) will be used to print the number of successes that will happen in one (size=1) experiment comprising of n number of trials with probability/proportion of success being p. Tossing a …
Beta Distribution Example for Cricket Score Analysis

This post represents a real-world example of Binomial and Beta probability distribution from the sports field. In this post, you will learn about how the run scored by a Cricket player could be modeled using Binomial and Beta distribution. Ever wanted to predict the probability of Virat Kohli scoring a half-century in a particular match. This post will present a perspective on the same by using beta distribution to model the probability of runs that can be scored in a match. If you are a data scientist trying to understand beta and binomial distribution with a real-world example, this post will turn out to be helpful. First and foremost, let’s identify the random variable that we would like …
How to Print Unique Values in Pandas Dataframe Columns
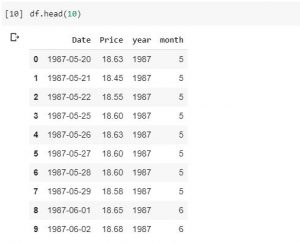
A quick post representing code sample on how to print unique values in Dataframe columns in Pandas. Here is a data frame comprising of oil prices on different dates which column such as year comprising of repeated/duplicate value of years. In the above data frame, the requirement is to print the unique value of year column. Here is the code for same. Note the method unique()
Pandas – How to Extract Month & Year from Datetime
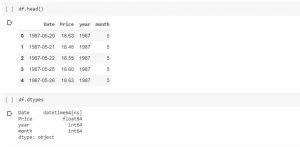
This is a quick post representing code sample related to how to extract month & year from datetime column of DataFrame in Pandas. The code sample is shown using the sample data, BrentOilPrices downloaded from this Kaggle data page. Here is the code to load the data frame. Check the data type of the data using the following code: The output looks like the following: Date object Price float64 dtype: object Use the following command to change the date data type from object to datetime and extract the month and year. Printing data using head command would print the following:
Pandas – How to Concatenate Dataframe Columns
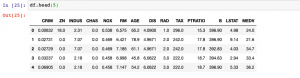
Quick code sample on how to concatenate the data frames columns. We will work with example of Boston dataset found with sklearn.datasets. One should note that data frames could be concatenated by rows and columns. In this post, you will learn about how to concatenate data frames by columns. Here is the code for working with Boston datasets. First and foremost, the Boston dataset will be loaded. Once loaded, let’s create different different data frames comprising of data and target variable. This above creates two data frames comprising of data (features) and the values of target variable. Here are the snapshots. Use the following command to concatenate the data frames. …
Difference between Machine Learning & Traditional Software
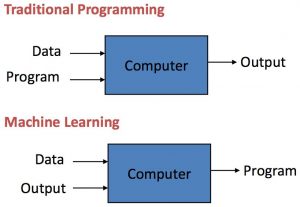
In this post, we will understand what are some of the key differences between machine learning models and traditional/conventional software. S.No Traditional Software Machine Learning 1 In traditional software, the primary objective is to meet functional and non-functional requirements. In machine learning models, the primary goal is to optimize the metric (accuracy, precision/recall, RMSE, etc) of the models. Every 0.1 % improvement in the model metrics could result in significant business value creation. 2 The quality of the software primary depends on the quality of the code. The quality of the model depends upon various parameters which are mainly related to the input data and hyperparameters tuning. 3 Traditional software …
Neural Network Architecture for Text-to-Speech Synthesis
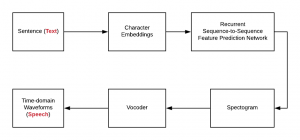
In this post, you would learn about a neural network reference solution architecture which could be used to convert the text to speech. The neural network solution architecture given in this post is based on deep learning (autoencoder network (encoder-decoder) with attention). Neural Network Reference Architecture for Text-to-Speech Synthesis In the solution architecture diagram (figure 1) depicted below, the following is described: Sentences are first converted into character embeddings. Character embeddings are numeric representations of words. Numeric representations of each of the words could be used to create numeric representations of higher-level representations like sentences/paragraphs/documents/etc. Character embeddings are next fed into recurrent sequence-to-sequence feature prediction network with attention. The sequence-to-sequence …
Reverse Image Search using Deep Learning (CNN)

In this post, you will learn about a solution approach for searching similar images out of numerous images matching an input image (query) using machine learning / deep learning technology. This is also called a reverse image search. The image search is generally searching for images based on keywords. Here are the key components of the solution for reverse image search: A database of storing images with associated numerical vector also called embeddings. A deep learning model based on convolutional neural network (CNN) for creating numerical feature vectors (aka embeddings) for images A module which searches embeddings of an input image (query) from the image database based on the nearest neighbor …
Why Data Scientists Must Learn Statistics?
In order to understand the need for data scientists to be very good at the statistical concepts, one needs to clearly understand some of the following: Who are data scientists? What is the need for statistics in data scientists’ day-to-day work? Who are Data Scientists? Data Scientists are the primarily Scientists who do experiments to find some of the following: Whether there exists a relationship between data Whether the function approximated (machine learning or statistical learning model) from a given sample of data could be generalized for the entire population In case there are multiple function approximations for predicting outcomes given a set of input, which one of the function approximation …

I found it very helpful. However the differences are not too understandable for me