Author Archives: Ajitesh Kumar
Mobile Apps Testing Frameworks Used at LinkedIn

The article lists down tools & frameworks that are used for mobile app testing at LinkedIn. Vows: Vows is a behavior driven development framework for Node.js. It is used to do asynchronous testing with Node.js. The primary feature of the framework is its support for asynchronous testing with Node and, the ability to run concurrent tests. Vows also supports code coverage reporting. Robotium: Robotium is an Android test automation framework that has full support for native and hybrid applications. It supports black-box UI tests for android applications. It is used to test native LinkedIn android app. Selenium: Selenium is used to automate end-to-end testing with mobile web browsers. FoneMonkey: FoneMonkey …
How to Measure Software Development Productivity
The article lists down pages/papers on measuring software development productivity. The Theory of Constraints: A good read on measuring software development productivity Measuring Productivity of Software Development Teams: The paper lists down different techniques/models for measuring software development productivity. CannotMeasureProductivity: Then, there is this article by Martin Fowler which says that it is difficult to measure software development productivity. He points about ineffectiveness of following approaches of measuring developer’s productivity: Lines of codes (LOC) Function points The software development teams working based on Waterfall model or Agile methodologies model tend to measure the developer’s productivity in terms of following variants: Function Points Story Points (size) vs Velocity Following pages present …
List of Javascript Templating Engines & Why One Needs Them?

The article presents a short overview on why one needs Javascript templating engines and, a list of these frameworks. Please feel free to suggest one or more frameworks if I missed to include them in the list below. Why do I ever need Javascript templating engine? Consider the following use-case scenario. Let’s say, you are a big enterprise with different line of businesses (LOBs). Each LOB has a set of web applications serving its business needs. With different LOB having different applications, following scenario is likely to happen: One particular LOB, X, has applications written with Java/JSP. Other LOB, Y, has applications written with .NET technology Other LOB, Z, …
Why Facebook Relies on A/B Testing?
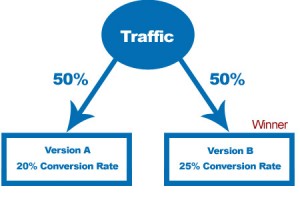
This article talks about A/B testing, why companies like Facebook rely on it and what would it take to adopt such testing for your website. What is A/B testing? A/B testing is a strategy in marketing in which two versions, A and B, (the control and the treatment) are tested against each other. A/B testing, as the names implies, is a simple randomized experiment with two variants/versions, A and B, one of which version A might be currently used version (control) and, version B (treatment) is modified in some respect to study/test the users’ behavior. These tests are also called as split tests. These tests involve modification some of the following …
Lessons from Evernote Usage of Apache Thrift Framework

This article throws light on underlying technology used by Evernote to meet the primary requirement of having client applications on different OS platforms connect to server application for accessing/updating the notes. What is Evernote? As per Wikipedia…Evernote is a suite of software and services designed for notetaking and archiving. A “note” can be a piece of formatted text, a full webpage or webpage excerpt, a photograph, a voice memo, or a handwritten “ink” note…. Evernote supports a number of operating system platforms (including OS X, iOS, Chrome OS, Android, Microsoft Windows, Windows Phone, BlackBerry, and webOS) and also offers online synchronisation and backup services. The diagram below illustrates …
Why Amazon.com Pages Rely on DNS Pre-fetch

The article presents a perspective on why Amazon.com pages rely on DNS pre-fetch and what other e-commerce websites could learn from this. Whats Happening Under the Hood? As you do the view source of the homepage, amazon.com, you would find following Javascript code snippet, right at the top of the page: <meta http-equiv=”x-dns-prefetch-control” content=”on”> <link rel=”dns-prefetch” href=”http://g-ecx.images-amazon.com”> <link rel=”dns-prefetch” href=”http://z-ecx.images-amazon.com”> <link rel=”dns-prefetch” href=”http://ecx.images-amazon.com”> <link rel=”dns-prefetch” href=”http://completion.amazon.com”> <link rel=”dns-prefetch” href=”http://fls-na.amazon.com”> Later, in the same page as well as other pages, you would find several resources such as images, Javascript, CSS files accessed from one of the above as base URLs. So, let’s try and explore some of the …
Javascript Frameworks used in LinkedIn.com

The article lists down different Javascript frameworks that have been used in LinkedIn web UI and mobile app. Following are some of the key Javascript frameworks that have been used in various different LinkedIn applications (Web & Mobile). If you disagree with one or more of these frameworks, please shout out loud. Also, feel free to suggest of frameworks that I missed to include. Sorry for any typos/misspellings as you read further. Dust.js Dust.js, the client-side templating engine, is used to serve LinkedIn webpages with common UI code for different web-apps products. These web-apps products are created using varied technology stack including Java/Grails/JRuby etc. With Dust.js, LinkedIn moved from …
LinkedIn Application Architecture – Software Distribution View

The article lists down the softwares used at different layers in the LinkedIn platform layered architecture. Presentation Layer Dust.js (Client-side templating JS engine) Backbone.js (Client-side MVC JS framework) JQuery YUI Library (UI libraries started by Yahoo engineers) Google V8 Engine (Used as server side JS templating engine) Node.js (Used in mobile app) HTML5 (Used in mobile app) Business Layer Java (Applications such as Profile) Grails (Applications such as a Recruiter app) JRuby (Applications such as a Skills app) Spring (Component Model) Scala Middleware Apache Kafka (Distributed entreprise-level messaging system) Data Layer Oracle (RDBMS as primary data store used for writes) Espresso (NoSQL data store emerging as primary data store and envisioned to …
OWASP Security Misconfiguration Example – Infosys Career Website

The article presents an example of “Security Misconfiguration” vulnerability that was found on Infosys career website. It could be noted that security misconfiguration is considered as one of the OWASP top 10 security vulnerabilities. The vulnerability was found with Careers web application of Infosys, which can be accessed at https://careers.infosys.com/. As you access the career site link, you would see the title icon as “SAP”. This does suggest that Infosys careers web application is created on top of SAP career module. The way I found that is following: Go to job opportunities page. Click on “Register”. You would land on the registration page with following link: https://careers.infosys.com/sap/bc/webdynpro/sap/hrrcf_a_candidate_registration Go ahead and strip the hrrcf_a_candidate_registration from …
Data Architecture Lessons from LinkedIn.com Data Handling Mechanisms

The article aims to describe how data is managed at LinkedIn.com, the most popular professional social networking site. Please shout out loud if you disagree with one or more of the aspects mentioned below. Also, do suggest if I missed on one or more aspects. Data use-cases at LinkedIn.com Following are some of the data use-cases that we may have come across while we are surfing various different LinkedIn pages: Update your profile, and the same appears in recruiter search in near real-time. Update your profile and same appears as network connections in near real-time. Share an update, and same appears on others news feed page in near real-time. Then, there are …
Reasons Why You Need Log Management Tools like SPLUNK

The article lists down reasons why one would want to use tools such as Splunk which primarily analyses logs (server, application etc) and create reports/events to be processed by different stakeholders. Log Management Tools – High Level Architecture Log management tools primarily aggregate logs from different servers including application, database, messaging servers etc and send the same to a centralized server which then analyzes and index the logs in the database. The end user can then log onto the console of these tools and analyze the reports created on top of these logs. Following diagram represents a very high level architecture along with end users classification: Following are some of …
Artificial Intelligence – Where to Put Your Time & Money

As I looked around some of the artificial intelligence (AI) related acquisitions in last few years, I got convinced, at least, on the fact that majority of large companies such as Google, Facebook, IBM are seeing various different artificial intelligence topics to play a key role in impacting end users’ life (and hence, developers) in the future. With that as the background, it gave me good enough reasons to start doing research in relation with following: As students, what topics of artificial intelligence should they take up as one of their computer science courses while selecting under-graduate & post graduate courses? As developers/programmers, what topics of artificial intelligence should they …
Java Interview Questions (Part 1) – Rookies Series

The article (first in the series) aims to present some tricky interview Java questions that could help you score high in your next Java interviews: Programming fundamentals Question: What is difference between object-oriented programming and functional programming? Answer: Following pages present good perspective on the differences: http://stackoverflow.com/questions/6720348/difference-between-oop-and-functional-programming-scheme http://c2.com/cgi/wiki?OoVsFunctional Java Objects Question: What is difference between comparing two objects using equals method and “==” operator? Answer: http://stackoverflow.com/questions/5848370/equals-and-operator-in-java Question: What is the significance of equals and hash method in Object class? Answer: http://www.javaworld.com/article/2074996/hashcode-and-equals-method-in-java-object—a-pragmatic-concept.html Collections Question: What is difference between LinkedList and ArrayList? When would you want to use one and not the other? Answer: http://javarevisited.blogspot.in/2012/02/difference-between-linkedlist-vs.html Question: How come you …
Can Artificial Intelligence be the Next Big Bet for Developers?
The article presents an analysis on what’s trending in the world of artificial intelligence thereby providing food for thought for the developers if they would want to bet on engineering field such as artificial intelligence and develop their expertise around that. What is Artificial Intelligence? Artificial intelligence (AI) is the intelligence exhibited by machines or software, and the branch of computer science that develops machines and software with human-like intelligence. Read further on the Wikipedia page. In this article, we shall primarily focus upon the software that could have human-like intelligence. Following are some of the characteristics of AI-based software: Maintain ontology of knowledge representing concepts and their relationships. Should have …
What’s Needed to Get Your Code Quality Match ISO Standard 25010

The article relates software quality characteristics defined by ISO 25010 standard (SQUARE) with code quality and, recommends on what could be done by the developers to write the code matching the ISO quality standards. SQUARE stands for Software QUAlity Requirements and Evaluation (SQUARE). Please feel free to comment and add further points in any of the sections pertaining to quality characteristics listed later below. As per ISO 25010 (SQUARE) standards, Software quality can be defined, managed and measured in terms of following two broad categories: Quality in Use: Relates to the outcome of human interaction with the software Product Quality: Relates to the static & dynamic properties of the software …

I found it very helpful. However the differences are not too understandable for me