Author Archives: Ajitesh Kumar
10+ Key Stages of Data Science Project Life cycle
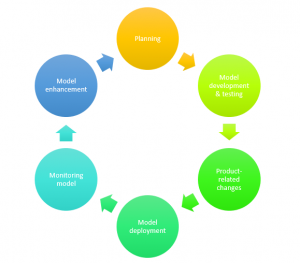
Data science projects need to go through different project lifecycle stages in order to become successful. In each of the stages, different stakeholders get involved as like in a traditional software development lifecycle. In this post, you will learn some of the key stages/milestones of data science project lifecycle. This article is aimed to help some of the following project stakeholders who play key roles in data science project implementation: Product managers Project managers ML architects The following represents 6 high-level stages of data science project lifecycle: Planning Model development & testing Product-level changes Model deployment Monitoring the model Model Enhancement Data Science Project Lifecycle – Planning ML Problem identification: …
N-Gram Language Models Explained with Examples
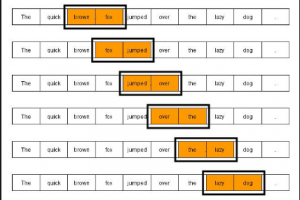
Language models are models which assign probabilities to a sentence or a sequence of words or, probability of an upcoming word given previous set of words. Language models are used in fields such as speech recognition, spelling correction, machine translation etc. Language models are primarily of two kinds: N-Gram language models Grammar-based language models such as probabilistic context-free grammars (PCFGs) In this post, you will learn about some of the following: Introduction to Language Models N-Grams language models Introduction to Language Models Language models, as mentioned above, is used to determine the probability of occurrence of a sentence or a sequence of words. Language models are created based on following …
Blockchain – Bitcoin Explorer Relaunched
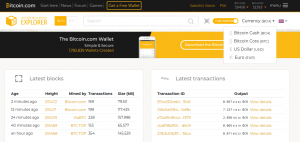
Here is the newly launched portal, https://explorer.bitcoin.com/bch for getting details on Bitcoin (BTC) and Bitcoin Cash (BCH). Front page displays details on latest blocks and transactions. One could easily analyze transactions, blocks, and addresses on both the Bitcoin Cash (BCH) and Bitcoin Core (BTC) chains. All you need to do is select the type of cryptocurrency (BTC or BCH) in the top right vertical menu and you would be able to see the transactions and related details of that specific blockchain. Currently, bitcoin blockchain explorer is supported in five different languages: English Hindi Svenska Chinese Russian Note that Bitcoin cash (BCH) is a cryptocurrency which is used on the Blockchain …
What Blockchain can do and What it can’t do?

Blockchain is a continuously growing list of records, called blocks, which are linked and secured using cryptography. Each block typically contains a hash pointer as a link to a previous block, a timestamp and transaction data. By design, a blockchain is inherently resistant to modification of the data. Simply speaking, Blockchain helps in decentralizing the ledger or data or database with the help of cryptography. The blockchain is also called as distributed ledger technology. Some of the famous blockchains are Bitcoin blockchain, Ethereum, Bitcoin Cash, Litecoin etc. In this post, you will learn different aspects related to what Blockchain can do and what it can not do. On the lighter …
Quick Introduction to Smoothing Techniques for Language Models

Smoothing techniques in NLP are used to address scenarios related to determining probability / likelihood estimate of a sequence of words (say, a sentence) occuring together when one or more words individually (unigram) or N-grams such as bigram([latex]w_{i}[/latex]/[latex]w_{i-1}[/latex]) or trigram ([latex]w_{i}[/latex]/[latex]w_{i-1}w_{i-2}[/latex]) in the given set have never occured in the past. In this post, you will go through a quick introduction to various different smoothing techniques used in NLP in addition to related formulas and examples. The following is the list of some of the smoothing techniques: Laplace smoothing: Another name for Laplace smoothing technique is add one smoothing. Additive smoothing Good-turing smoothing Kneser-Ney smoothing Katz smoothing Church and Gale Smoothing …
Blockchain Architect – A Sample Job Description

Blockchain application development is going mainstream, and hence, would be requiring professionals with different roles and responsibilities including Blockchain architect, Blockchain developer etc. You may want to check out different Blockchain job designations on this page. The following is a list of points which can be made part of job description for Blockchain architect and related designations such as Blockchain platform architect, Blockchain solution architect, Blockchain lead architect etc. Demonstrate good understanding of Blockchain fundamentals, smart contracts, consensus algorithms Good understanding of different types of Blockchain such as public, private/permissioned, public permissioned etc. Good understanding of Blockchain framework such as Hyperledger Fabric, R3 Corda, Ethereum (Solidity) Good understanding of various …
Quantum Superposition States Explained with Examples
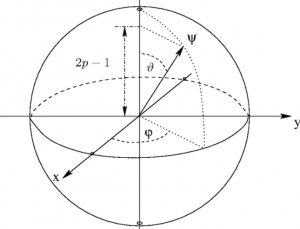
Qubit (Quantum Bit) is the fundamental unit of information in quantum computing as like bit which is the basic unit of information in classical computing. However, unlike bit in the classical computing which can exist in one of two states such as 0 and 1 at any given point of time, the qubit can be found to exist in states 0, 1 or the superposition state which, simply speaking, can be said to be both 0 and 1. In this post, you will learn some of the following: Qubit and Superposition State Superposition state explained with examples Qubit and Superposition State The following are some of the important points about …
Cheat sheet – 1500 Cryptocurrency Tokens / Coins & Details – Part 4

This post lists down some of the following information related to different cryptocurrency coins/tokens. This could be used as a quick reference/cheat sheet to get quick information about any specific cryptocurrency coin. Token name Ticker Symbol used in cryptocurrency exchanges Company’s Website Explorer where details in relation to coins, tokens can be found Source code (Github) Twitter handle List of 400 Cryptocurrency Tokens / Coins S.No Token Name Explorer Source Code Twitter 1101 Cannation (CNNC) Explorer 1 GitHub 1102 Dogecoin (DOGE) Explorer 1 GitHub @dogecoin 1103 Delphy (DPY) Explorer 1, Explorer 2 GitHub @delphy_org 1104 MicroMoney (AMM) Explorer 1, Explorer 2 GitHub @micromoneyio 1105 AnarchistsPrime (ACP) Explorer 1 GitHub …
Cheat sheet – 1500 Cryptocurrency Tokens / Coins & Details – Part 3

This post lists down some of the following information related to 400 different cryptocurrency coins/tokens. This could be used as a quick reference/cheat sheet to get quick information about any specific cryptocurrency coin. Token name Ticker Symbol used in cryptocurrency exchanges Company’s Website Explorer where details in relation to coins, tokens can be found Source code (Github) Twitter handle List of 400 Cryptocurrency Tokens / Coins S.No Token Name Explorer Source Code Twitter 701 Sparks (SPK) Explorer 1 GitHub @Sparks_Crypro 702 ALQO (ALQO) Explorer 1, Explorer 2 GitHub @ALQOCOIN 703 Curecoin (CURE) Explorer 1 GitHub @CureCoin_Team 704 NVO (NVST) Explorer 1 GitHub @nvoexchange 705 IslaCoin (ISL) Explorer 1 GitHub …
Cheat sheet – 1500 Cryptocurrency Tokens / Coins & Details – Part 2

This post lists down some of the following information related to different cryptocurrency coins / tokens. This could be used as a quick reference/cheatsheet to get quick information about any specific cryptocurrency coin. Token name Ticker Symbol used in cryptocurrency exchanges Company’s Website Explorer where details in relation to coins, tokens can be found Source code (Github) Twitter handle List of 400 Cryptocurrency Tokens / Coins S.No Token Name Explorer Source Code Twitter 301 SwagBucks (BUCKS) Explorer 1, Explorer 2 GitHub @SwagSociety_me 302 Etherparty (FUEL) Explorer 1, Explorer 2 GitHub @etherparty_com 303 Ripio Credit Network (RCN) Explorer 1, Explorer 2 GitHub @RCN_token 304 Revain (R) Explorer 1, Explorer 2 …
Cheat sheet – 1500 Cryptocurrency Tokens / Coins & Details

This post lists down some of the following information related to different cryptocurrency coins/tokens. This could be used as a quick reference/cheat sheet to get quick information about any specific cryptocurrency coin. Token name, Ticker Symbol used in cryptocurrency exchanges, Company’s Website Explorer where details in relation to coins, tokens can be found Source code (Github) Twitter handle This post lists down 300 tokens. The remaining 1200 tokens are split into another 3 pages such as below: 300-700 Cryptocurrency Tokens 700-1100 Cryptocurrency Tokens 1100-1500 Cryptocurrency Tokens List of 300 Cryptocurrency Tokens / Coins S.No Token Name Explorer Source Code Twitter 1 Primalbase Token (PBT) Explorer 1 @primalbasehq 2 CHIPS (CHIPS) …
How to Setup Apollo Graphql Client with Angular

Apollo Client is a GraphQL client for Angular, JavaScript, and native platforms such as some of the following. Apollo client for Angular is used to build Angular UI components that fetch data with GraphQL. Javascript React VueJS Meteor Ember Polymer Native platforms Native iOS with Swift Native Android with Java In this post, you will learn about setting up Apollo GraphQL client for using it in your Angular App. Instructions on setting up Apollo GraphQL Client with Angular App The instructions given below is worked out with the Angular 4.* app. However, this should also apply to the Angular 5 and later angular versions’ app. As per instructions on this …
Blockchain Architect – Top 20 Project Implementation Considerations

When everyone is considering implementation different projects using Blockchain (distributed ledger) technology, it becomes key for Blockchain architects and leaders to pay attention to some of the key considerations including challenges related with blockchain projects implementation. On the lighter note, the comic strip below is a representation of the need for Blockchain architects required to get into several details including different architecture considerations before starting on a blockchain projects. In this post, you will learn about key considerations to be made by Blockchain architects and leads before starting on the Blockchain projects. Blockchain Project Implementation – Key Considerations Learning from similar project implementations: Analysis of blockchain-related implementations in similar and/or …
Blockchain Use case: Monitoring Global Climate Change

United Nations Climate Change secretariat recently announced that it would be supporting usage of distributed ledger technology (DLT) aka Blockchain for monitoring global climate change. In this relation, on 12 December 2017 in Paris, a multi-stakeholder group of 25 organizations working on distributed ledger technology (DLT, i.e. blockchain) held a meeting to agree to collaborate and establish an open global initiative called the Climate Chain Coalition (CCC). Given that Global climate change is an issue which needs a lot of trust and transparency between participating countries, Blockchain technology forms the key. Here is a comic strip which represents the same. In this post, you will learn about aspects of climate …
Electron uses Blockchain Technology for innovating Energy Sector

Electron, a blockchain-based startup out of UK, is innovating in the energy sector for enabling the energy creators (such as micro-grids and mini-grids) to trade energy with those requiring energy while ensuring data security, transparency and traceability/provenance. The company has got experts from the areas of blockchain energy and e-trading coming together and building innovative products for achieving some of the following objectives in relation to energy creation and trading: Decentralization: The idea is that Energy production and distribution should no longer be limited to the large enterprises (especially government ones). Given the ease with which one can generate renewable energy sources such as sun and wind, one should be …
Cryptocurrency – Bitcoin and Bitcoin Cash Difference

Bitcoin is the first decentralized digital cryptocurrency which can be transacted between different users without the need for a trusted centralized bank. The bitcoin transactions are recorded in a shared distributed ledger which is maintained by the computer nodes (peer nodes) in a peer-to-peer (P2P) network. The underlying technology is called as distributed ledger technology (DLT) or Blockchain. The ticker symbol for Bitcoin is BTC. Last year in 2017, Bitcoin Cash came into existence. Having similar names, it may get confusing as to whether they are same? Can Bitcoins be converted into Bitcoin Cash based on any formula? Well, Bitcoin and Bitcoin Cash are different. If you have come across …

I found it very helpful. However the differences are not too understandable for me