Category Archives: Application Security
What is OAuth-based Authentication?

Although there are several articles on the internet on OAuth including the pages on http://www.oauth.net , I was unable to understand the concept behind OAuth by going through any one of those pages and instead kept wandering to several pages. Maybe, because I was impatient soul and wanted to land onto one page which could help me understand it all at just one page without me to wander another set of pages including image searches in Google for keyword “oauth” or “oauth authentication”. The only pages which matched my appetite is http://hueniverse.com/oauth/ . However, one has to patiently go through all of these pages to understand OAuth. This is quite …
Tips for Setting up Application Security Education/Training Plan

The article represents one of the education model that could be used to regularly educate your IT organization/team about latest security updates, attack patterns, mitigation techniques, security-related libraries and infrastructure, best practices and guidelines, etc . Now that application security is becoming an important aspect to take care, while laying out plan for application design and development, it becomes much more important to put a plan in place for educating application developers & testers. The primary objective is to create a security-aware development team (organization at large). Following is one of the model that could be used to achieve the above said objective: Security Awareness Training: Security awareness training to all …
Design Tips for Developers to Secure Cloud Applications

If you are a developer working on one or more cloud applications and want to know design and coding tips to make sure that you take care of appropriate security concerns, following represents some of the important areas to consider: Data Design: Data design is one of the key areas of concerns when one is developing cloud applications. This is primarily because cloud service model such as SAAS (Software-as-a-service) allows data related with different customers to be hosted on same database server. And, if data model, primarily related with multi-tenancy, is not designed in the nice manner, there are high possibilities of data breach wherein the attacker could get access …
Samsung Fingerprint Scanning API & Mobile Wallet Security?
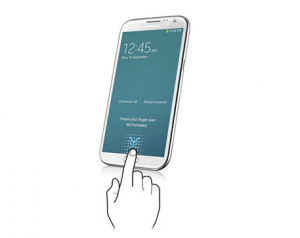
This article explores the recently released Samsung fingerprint scanning API also termed as “Pass API” in light of security for mobile wallets. Pass API is released as part of the Samsung Mobile SDK 1.5 beta1 during the launch of Samsung Galaxy S5 mobile phone. One of the key feature of Samsung galaxy S5 is fingerprint reader. The application could use fingerprint reader to scan user fingerprints and verify against the users’ stored fingerprints on the device. This article presents an overview on the PASS API and, then, talks about how it could be used for mobile wallets’ security. What is Pass API? As mentioned on Samsung Developers Page for Pass API, …
OWASP Security Misconfiguration Example from PayPal.com

The article represents some of the examples of OWASP security misconfiguration vulnerabilities that I could figure out by spending sometime on the Paypal.com website. The article is just an educational one and is not written with any other intention. If you are from Paypal reading this, please get it right. Accessing PayPalObjects.com with URL, https://www.paypalobjects.com/ displays the fact that it is hosted on Apache Server. Take a look at the picture below. It looks like paypalobjects.com server hosts static resources such as CSS, JS and images file as I could figure out several of such resources link with base URL as paypalobjects.com. Password Recovery Module seems to be using Spring Webflow …
Top 4 Security Books Developers Would Want to Keep Handy

Off-late I have been doing an extensive research on application security to to come up with application security guidelines (minimum & most important ones) which could prove very handy and at the same time, very useful for different class of IT professionals including developers, and architects. This is where I have come across some of the following books which has helped me to fulfill my objectives. In one of my later blogs, I shall also list down those basic minimum knowledge that is needed by developers to write secure code. In the meantime, allow me to list down top 4 application security books that, I believe, every developer would want …
List of Application Security Forums/Groups You Would Want to Frequently Visit

If you have been looking out to explore (as depicted by diagram below:-) various different application security forums to keep yourself updated with latest application security discussions, following is the list of security forums you may want to visit frequently and get yourself involved to remain up-to-date with application security: Online Forums http://www.coderanch.com/forums/f-65/Security: Very active & popular forum, this is primarily a place for Java developers to discuss on security topics related with Java. http://www.is-ra.org/forum/: Not very active though, however, this is a place for information security professional who are more interested in discussion topics related with some of the following: Ethical hacking & penetration testing Digital forensics Cryptography and …
Top 5 Bad Application Security Practices

We all come across good security practices and make ourselves familiar with them to develop secured code. However, it may also be good idea at times to know about some of the bad security practices such that we, for sure, try and avoid them. [adsenseyu2] Following are top 5 bad practices you may want to know about: Do NOT interact with un-trusted programs: Make sure that the external programs that your program is invoking for reasons such as data or functionality, must have got reviewed and tested for security compliance. One of the common entry points into secured applications are these unsecured applications and hackers just love them. Hackers, …
Developer Analysis of Hacker’s Attack on Target Stores – Page 1

This is a series of articles to represent developer’s point of view and learning from recent TARGET retail store security attack due to which various reports say that around 40 million customer credit and debit cards data must have got compromised. This hackers’ attck is currently talk of the town and is under analysis of various different security agencies including US secret service. In this article, we shall look at various different possibilities/attack vectors/security vulnerabilities that could have led to third attack. One of the many possibilities could have been installation of malware at the POS system where customers use to swipe their card for the purchases that they make. This could have …
Top 7 Secured Practices for Securing Your Partner APIs

If you are planning to publish partner APIs for exposing your business services or data to your partners and customers, you may want to consider following top 7 secured best practices to ensure application level security: [adsenseyu2] Access-token based Authentication: Have your partners’ applications authenticate itself (and its users) using access-tokens rather than actual passwords. This is because access-tokens may be easily time-boxed and can be enforced to be renewed at the regular time-intervals. And the theft of access token can not really compromise the actual users’ password with the parent application. In this relation, you may consider using OAuth based authentication technique. In addition to usage of access-token for …
OWASP Security Misconfiguration – Classic Example – 1

[adsenseyu2] One of the OWASP top 10 application security vulnerability is Security Misconfiguration. One of the most common way to identify the security misconfiguration configuration is to check if error handling reveals stack traces or other informative error messages to users. I tried and run an automated scanner on this website, http://www.davrohini.org/ and got various different URLs which revealed stack traces including some of the following: http://www.davrohini.org/user/users.jsp http://www.davrohini.org/user/snews.jsp http://www.davrohini.org/user/left.jsp However, the most dangerous one of the above is http://www.davrohini.org/user/left.jsp. Take a look at the screenshot below. Security Misconfiguration Example – Showing compilation errors Take a look at another diagram below that shows the information regarding the server Apache Tomcat …
Tips for Gathering Security Requirements of your Web Application Project

Gathering security requirements in relation with a project, sprint (if agile) is key to deliver secured applications. This is because security requirements would lead to appropriate design in relation with security. Following are key topics to consider for gathering security requirements: Authentication & password management: This is mostly a one-time activity and done as the start of the project and not in every sprint. One may want to ask questions such as following in relation with authentication and password management: Password policies: This is important to ask to avoid dictionary attack in relation with user credentials. Password hashing: This is important to make sure password is encrypted with appropriate encryption …
Top 7 Security Attack Questions While Analyzing Every Requirement

Following are top 5 security attack related questions that you could ask while analyzing the each requirement in hand, the answers to which could help you put better design in relation with security: Security threats analysis related with data entering into/coming out of the system: How could an attacker inject SQL commands? (OWASP SQL Injection). Solution: Use parameterized SQL queries rather than building SQL statements dynamically using string concatenation How could an attacker perform a cross-site scripting attack? (OWASP Cross-Site Scripting – XSS). Solution: Use OWASP ESAPI to sanitize user input against scripts such as Javascript that could lead to XSS attacks. This is more about doing input data validation as soon as …
Tips for Designing Security for Your Public APIs

[adsenseyu2] Before we look into tips & techniques to design security for your Public APIs, lets understand what do we mean by Public APIs? Public APIs are APIs that are published to the world including developers, or partners’ developers to create their custom application by making use of APIs. These APIs can be used by another program, mobile apps or web applications (Web UI), desktop client etc. Following are some tips/techniques for designing security for your Public APIs: IP Address Restrictions: To be able to control access to APIs based on IP address from which request arrived, the IP address restrictions policy should be imposed. This is very handy when …
List of Threat Modeling Tools
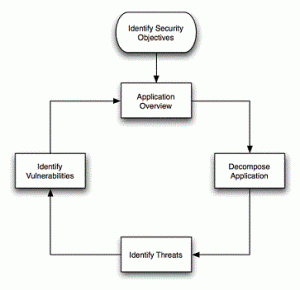
Threat modeling tools are used to perform systematic analysis of attack vectors by helping you analyze some of the following questions: Which are high-value assets? What does attacker profile may look like? Which are most vulnerable areas in the application which can be attacked by the hackers? What are most relevant threats to the application? Are there one or more attack vectors which can go unnoticed? Following is the list of top 5 threat modeling tools you may keep handy for threat modeling: Microsoft Free SDL Threat Modeling Tool: Tool from Microsoft that makes threat modeling easier for all developers by providing guidance on creating and analyzing threat models. Following diagram displays …
My All-Time Web Application Security Favorites

Following are my all time favorites web pages I frequently visit for remaining up-to-date with web application security: https://www.owasp.org/ Website I frequently visit to check out videos, presentations, Books etc. http://bsimm.com/ Website about building security in maturity model http://www.webappsec.org/ Website representing Web Application Security Consortium that publishes technical information, contributed articles, security guidelines, and other useful documentation. Businesses, educational institutions, governments, application developers, security professionals, and software vendors all over the world utilize their materials to assist with the challenges presented by web application security. Books: List of web application security books you would want to keep handy Web Application Security Interview Questions: List of some interesting web security interesting …

I found it very helpful. However the differences are not too understandable for me