Author Archives: Ajitesh Kumar
Google PACO for Tracking Trends on Personal Stuff

The article talks about features & benefits of Google PACO mobile app that one could use for tracking analytics data in relation with personal stuff. Thanks for reading it further. Ever wanted to check on how are you doing in relation with some of the following habits on the personal front: Software Developer: How much time are you devoting on some of the following: Learning new technologies by reading one or more webpages/books Trying out/evaluating new tools & frameworks (this could be tracked on weekly basis rather than daily basis) Physical Training (PT): How much time are you spending daily on doing one or more PT exercises such as running? In …
OWASP Security Misconfiguration Example from PayPal.com

The article represents some of the examples of OWASP security misconfiguration vulnerabilities that I could figure out by spending sometime on the Paypal.com website. The article is just an educational one and is not written with any other intention. If you are from Paypal reading this, please get it right. Accessing PayPalObjects.com with URL, https://www.paypalobjects.com/ displays the fact that it is hosted on Apache Server. Take a look at the picture below. It looks like paypalobjects.com server hosts static resources such as CSS, JS and images file as I could figure out several of such resources link with base URL as paypalobjects.com. Password Recovery Module seems to be using Spring Webflow …
Tips to Quickly Get Started with Android Hello World!
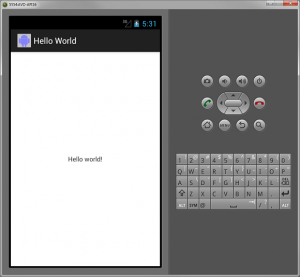
The article is written for those curious ones (Java developers at all level) who want to quickly get started with Android programming. This is what I did and got started with few hiccups (in relation with starting ADB server) to get the hello world done. Download right set of tool: Visited the android SDK download page where I got option to download appropriate libraries/tools based on whether I am using one of the existing supported IDE such as eclipse. Although, I am an experienced Java developer and use Eclipse, I rather went with downloading entire ADT bundle consisting of eclipse and SDK platform/tools. Choosing System Type: While I downloading I …
Tools & Frameworks That Were Used to Build WhatsApp (Android)

The article talks about the tools & frameworks that got used to build WhatsApp mobile application for Android platform. The reason why I decided to write this article is the acquisition of WhatsApp by Facebook in $19 billion and, my curiosity on what could have gone in building such application from technology perspective. The objective is to let Android developers take a peek into WhatsApp Android application and, get appropriate information on tools & frameworks that could be used to build a messaging application such as WhatsApp. Thanks for reading it further. Tools & Frameworks Used in WhatsApp Following is a list of tools & frameworks that were found to …
How Static Resources (CSS, JS) are Served at Facebook.com?

This article talks about techniques used at Facebook.com to serve the static resources such as CSS, JS and Images files when someone accesses Facebook.com. If you are one of the developer at Facebook and worked on related modules, and disagree with one or more aspects of this article, please drop a message and I shall change the same appropriately. The article is aimed to present a perspective on how to handle the web static resources, based on how it is handled at facebook.com. Thank you for reading it further. Back in February 2004? Well, like most other startups, facebook got launched in February 2004 with usual manners of serving CSS & JS …
Use Facebook BigPipe to Load Webpages Faster
This article represents Facebook BigPipe technology and various different open source frameworks which could be used to load web page faster like Facebook. Please suggest related frameworks if one or more of them is not mentioned in this article. You may have read the text on BigPipe on several webpages. However, I wanted to present a different perspective including pictorial presentation for better understanding. Traditional webpage serving model Following diagram represents traditional webpage serving model. You may notice that in traditional model, the request-response operations are pretty much sequential in nature. Thus, following can be observed: Webserver Busy, Browser Idle: As the request is sent from browser, and webserver …
What Javascript Frameworks are used at Twitter.com?

I have been doing research on what are some of the UI frameworks that are used at twitter.com. Following is a list of those UI frameworks, primarily Javascript. Please feel free to shout if you happen to know that one or more of the following frameworks ain’t actually used: Testing Jasmine: This is a javascript library. A behavior-driven development framework for testing JavaScript code. It does not depend on any other JavaScript frameworks. It does not require a DOM. And it has a clean, obvious syntax so that you can easily write tests. UI-based Sizzle: A pure-JavaScript CSS selector engine designed to be easily dropped in to a host library. Bootstrap: As …
Java Lambda Expressions Explained with Examples

The article represents different viewpoints on Java Lambda Expressions (Java 8) to help Java developers understand what, why, when, how of Lambda expressions. Lambda expressions are nothing but a way to abstract behavior unlike the object-oriented programming which is based upon the abstraction of data in form of object. Lambda expressions are used to assign the behavior to a variable or pass the behavior in between method calls instead of wrapping the behavior in an object and working with the objects. Take a look at the following example to understand the Lambda expressions better.Remember, the famous addActionListener method on button to capture the button-click event and, take action when the …
Infosys.com Website Design – A Post Mortem
This article represents some of the libraries, tools & framework one would want to use to create Infosys style website. Lets first try and re-iterate some of the key striking characteristics: Responsive Large fonts, vector icons Background image slider with diligently selected relevant images Following are some of the tools (libraries) & technologies (programming languages etc) that can be used to achieve some of the above: .NET programming language: The website is created with .NET programming language. Font Awesome 4.0.3: Font awesome is used for vector iconsfound at several places on the website. Fotorama image slider: The image sliders on homepage and various other pages is empowered by fotorama.js. Webtrends: Looks …
Why FlipKart.com used OpenSearch to Empower Its Shopping Search Engine

I had an interesting incidence few weeks back when I wanted to access flipkart.com and I opened Google Chrome browser, wrote the address flipkart.com and added a space to it. And, what I found was following: And, the next moment I wanted to know about how did they achieve this. Upon doing some research, I found that it is a set of OpenSearch technologies that let Google Chrome enabled something like above for flipkart.com. And, I was able to write query word such as mobile, and it showed up the search results for mobile phones. It did save me from going on to flipkart.com and write mobile in the …
5 Free Online Courses on Algorithms Developers May Want to Checkout

The article represents top 5 free online courses on algorithms developers may want to keep handy in order to get themselves stronger in data structure and algorithm concepts. I wanted to compile these links primarily because as a developer I always wanted to find out some of the great web pages/documents on the internet which could help me get stronger in data structure and algorithm. Hope the list below helps you to get up and running with algorithms. Algorithms, Part 1 Algorithms, Part 2 Introduction to Algorithms: This is an undergraduate course which is made open as part of open course ware initiative at MIT. This course provides an introduction to …
How to Measure Code Maintainability with Sonar

This article talks about 4 different quality parameters found on Sonar dashboard which could help measuring code maintainability. Following are those quality parameters: Unit Test Coverage: Unit Test Coverage depicts code coverage in terms of unit tests written for the classes in the project. Greater test coverage depicts that developers are focusing on writing good unit tests for their code which results in greater test coverage. This also depicts the fact that the code is testable and hence, easier to change as a bad change could lead the unit tests to fail and raise the red flag. And, a code easier to change becomes a code easier to maintain. One …
5 Tricky Interview Questions for Java ArrayList

I have been involved in many a java interviews and following are five tricky ones where I found several junior to mid-level Java developers faltering once in a while. Thus, I thought to put an article around these questions to help junior Java developers make familiar with these questions. The article presents the 5 tricky interview questions in relation with Java ArrayList, I believe, could get the interviewee score some browny points, if answered well. Let me know if you agree and would like to add another set of questions to the list below: How does the size of Arraylist increases automatically? Could you share the code? This is the most …
The 7 Habits of Highly Effective Developers

Well, I researched on the internet looking for one or more articles which was written with the title, 7 Habits of Highly Effective People, and found a couple of them that has been written in the recent past. Following are some of them: http://blogs.msdn.com/b/johnwpowell/archive/2008/05/22/the-7-habits-of-highly-effective-developers.aspx http://drupal.technicat.com/writing/programming.html http://css.dzone.com/articles/7-habits-highly-effective The above articles are good and do talk about different aspects of becoming effective developer. However, I was not satisfied much as I could not find mention on some of the points that I wanted to talk about. Following is representation of my views on 7 Habits of Highly Effective Developer. Please feel free to share your opinion on whether I was able to …
How to Increase Unit Test Coverage of Legacy Code?
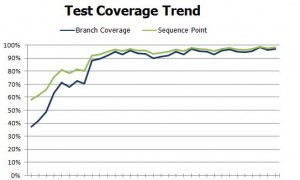
The article represents a time-tested approach on how to increase unit test coverage with legacy code. I shall try and answer following relevant questions in order to present the approach on increasing the test coverage of legacy applications (code). What are some of the key challenges? Leadership Buy-in: As soon as you start planning for writing unit tests on legacy applications, you come to realize that it won’t be very effective and smooth without the consideration of code refactoring. The reason being the fact that legacy code in many cases are found to have very high code complexity in terms of cyclomatic complexity and, familiar code smells such long classes, …
2014 Development Trend: Decouple User Experience from Functionality

The article represents an interesting trend in relation with need for decoupling user experience from functionality that is happening as result of different UI channels such as web, mobile devices using which users could access the software functionality. This can be termed as “Paradigm Shift” that needs to be adopted by developers sooner than later as part of the development practice. This is becoming much more relevant for this year, 2014 where there will be a need for delivering functionality on different devices/channels. What this means is that developers need to stop visualizing user interfaces (UIs) when they analyze the feature/functionality development. This is primarily because of the following reasons: …

I found it very helpful. However the differences are not too understandable for me