Tag Archives: owasp
OWASP Broken Authentication and Session Management Example
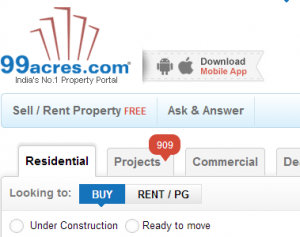
The article presents an example on one of the top OWASP vulnerability related with authentication and session management. This is termed as “Broken Authentication and Session Management”. To know more about this vulnerability and related details, visit OWASP page for broken authentication and session management. I was surfing a website, http://www.99acres.com, few days back and tried to retrieve my password using “Forgot Password” page. As I entered my username, I was amazed to see my email address shown there. I, then, tried another name such as “karthik” and following was the message:“An email has been sent to karthiksundaram@gmail.com. Please click on the link provided in the email to create …
OWASP Security Misconfiguration Example – Infosys Career Website

The article presents an example of “Security Misconfiguration” vulnerability that was found on Infosys career website. It could be noted that security misconfiguration is considered as one of the OWASP top 10 security vulnerabilities. The vulnerability was found with Careers web application of Infosys, which can be accessed at https://careers.infosys.com/. As you access the career site link, you would see the title icon as “SAP”. This does suggest that Infosys careers web application is created on top of SAP career module. The way I found that is following: Go to job opportunities page. Click on “Register”. You would land on the registration page with following link: https://careers.infosys.com/sap/bc/webdynpro/sap/hrrcf_a_candidate_registration Go ahead and strip the hrrcf_a_candidate_registration from …
OWASP Security Misconfiguration Example from PayPal.com

The article represents some of the examples of OWASP security misconfiguration vulnerabilities that I could figure out by spending sometime on the Paypal.com website. The article is just an educational one and is not written with any other intention. If you are from Paypal reading this, please get it right. Accessing PayPalObjects.com with URL, https://www.paypalobjects.com/ displays the fact that it is hosted on Apache Server. Take a look at the picture below. It looks like paypalobjects.com server hosts static resources such as CSS, JS and images file as I could figure out several of such resources link with base URL as paypalobjects.com. Password Recovery Module seems to be using Spring Webflow …
OWASP Security Misconfiguration – Classic Example – 1

[adsenseyu2] One of the OWASP top 10 application security vulnerability is Security Misconfiguration. One of the most common way to identify the security misconfiguration configuration is to check if error handling reveals stack traces or other informative error messages to users. I tried and run an automated scanner on this website, http://www.davrohini.org/ and got various different URLs which revealed stack traces including some of the following: http://www.davrohini.org/user/users.jsp http://www.davrohini.org/user/snews.jsp http://www.davrohini.org/user/left.jsp However, the most dangerous one of the above is http://www.davrohini.org/user/left.jsp. Take a look at the screenshot below. Security Misconfiguration Example – Showing compilation errors Take a look at another diagram below that shows the information regarding the server Apache Tomcat …
PHP Code for Avoiding XSS Attacks
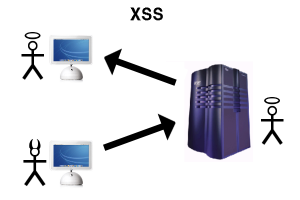
[adsenseyu2] Before we go and discuss the PHP coding tips and techniques to avoid Cross-site scripting (XSS) attacks, lets try and understand quickly what is XSS attack. XSS is a Web-based attack performed on vulnerable Web applications which ends up victimizing the end user rather than the application itself. In these attacks, malicious content is delivered to users primarily using JavaScript. The XSS attack happens when the web applications accepts the input from the end user without validating it. In XSS attack, the malicious code executes in the context of the victim’s session, allowing the attacker to bypass normal security restrictions. There are multiple good web pages to read about XSS …

I found it very helpful. However the differences are not too understandable for me