Category Archives: Application Security
Obamacare Website HealthCare.gov & Security Threats Review

Well, there have been lot of discussions around security issues with Obamacare website, healthcare.gov which has become talk of the town recently. The federal portal serves 36 states not operating their own health insurance exchanges. Fourteen other states and the District of Columbia run their own marketplaces. One of the factors attributing to security issues is sheer large volume of untested source code covering 500 millions lines of code. One of the most important security threat is related with information disclosure of the millions of Americans. The sensitive personal information of millions of Americans such as social security numbers (SSN), birthdays, incomes, home mortgages, and addresses is at risk. Another security …
Auditing Requirements are Tricky. Isn’t it?

[adsenseyu2] Many a project I worked upon, did not have a clear stated set of requirements related to auditing. Interestingly, with some projects, the auditing related requirements were created only after a couple of releases and got prioritized as less important in that specific release. One of the common observation I made across these projects is lack of understanding of auditing requirements and its significance, to key stakeholders including product owners, business analysts, developers and testers. Most of them could not figure out a strong reasoning in relation with why do we need to take care of audit trail of one or more transactions, until they got addressed/questioned by a …
Developers lack Application Security Skills. Do You Agree?

[adsenseyu2] In my experience, I have found that almost 95% of application developers lack application security skills and at times, tend to complete their journey without knowing much of the security technologies and related skills. Ask them if they wrote secured code, and almost in 90% of cases, they may say “don’t know” or say, “yes, wrote parameterized queries”. I talked to some of the developers at different experience levels and found some of the following as their answers: Use secured frameworks, so why bother?: Well, frameworks that are used for application development takes care of security aspects. So, we rely upon these frameworks for security concerns and not pay …
PHP Code for Avoiding XSS Attacks
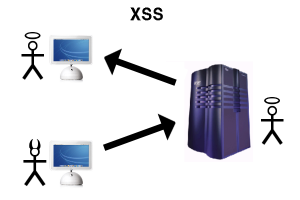
[adsenseyu2] Before we go and discuss the PHP coding tips and techniques to avoid Cross-site scripting (XSS) attacks, lets try and understand quickly what is XSS attack. XSS is a Web-based attack performed on vulnerable Web applications which ends up victimizing the end user rather than the application itself. In these attacks, malicious content is delivered to users primarily using JavaScript. The XSS attack happens when the web applications accepts the input from the end user without validating it. In XSS attack, the malicious code executes in the context of the victim’s session, allowing the attacker to bypass normal security restrictions. There are multiple good web pages to read about XSS …
How to Address Application Security in Agile Scrum Teams?
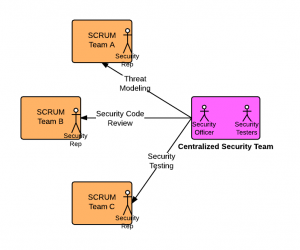
One of the concerns that takes the back burner while setting up the agile SCRUM teams is application security. One other area that gets similar behavior like security is performance which shall be addressed in later articles. However, performance gets addressed quickly as it is key quality characteristic and gets noticed by end users very quickly. In the traditional waterfall based development model, security gets fair attention as the non functional requirements related with security gets captured in the initial stages and the team gets composed of at least one security officer/specialist/architect to take care of security requirements. However, having a security specialist/officer in each SCRUM team is not feasible …
Top 6 things to Avoid Logging
Following are some of the things you may not want to write in the log file or write in masked form: Passwords (goes without saying) Database connection strings Encryption keys/access tokens Sensitive personal data Session identification value (must be masked) File Paths (consider masking)
Minimum Security Coding to do Before Your Website Launch
I am sure you are very excited to launch your website as soon as the coding for minimum functionality is complete. However, I would only suggest some of the following as bare minimum which you may consider as important things to be taken care before your website launch: Input validation: Some of the following OWASP top 10 vulnerabilities can be averted if only we do coding for input validation. You would give an argument that you actually do the input validation and what different you need to do. All I would say is what you do in form of input validation is one or more of business rules representing boundary …
Security Code Review Tips for Application Developers
One of the key aspects of secured application development practice is Security code review. Security code review, as like normal code review, could be done either in automated fashion using one or more tools, or in manual fashion where one or more developers are involved in doing code review. Unlike application normal code review where one needs the knowledge of business functionality and programming language & related technologies’ knowledge, Security code review requires knowledge on different aspects of security including some of the following: Common threats (STRIDE can be a great place to start understanding threats) Vulnerabilities (OWASP Top 10 describes most common vulnerabilities) Remediation techniques recommended in that programming …
Top Security Considerations for your Cloud Applications
I have been working/reviewing a cloud application where data security has been shown as top security concerns for most of the customers. Following are key areas for consideration when planning for security for your cloud applications: Internal theft: One of the most crucial security thefts come from unscrupulous employees who can pass/leak data to the competitors. The customers using the cloud applications are suggested to advise their employees on this front. Physical access control & monitoring: The physical access to the data center hosting the cloud application should be restricted and monitored at all times. Login access control: Only authenticated users should be allowed to login.In addition, the authenticated users …
Key Considerations for Application Security & Agile SCRUM Team Composition
Before going into the SCRUM team composition in relation with application security, it can be worth while knowing what are key aspects of secured application development practices: Security awareness training Threat modeling Secured coding practices Secured code reviews Security testing Achieving the state of secured application development practices is one of the toughest challenges for most SCRUM MASTERS to crack. For achieving secured application development, different alternatives could be explored to build the team, depending on software development methodology including agile and non agile methodologies. For agile development based on SCRUM model, following alternatives can be explored: Security Officer/Adviser/Architect: The role of the security adviser is to counsel various SCRUM teams …
Top 5 Secured Application Development Practices
Following are top 5 areas to consider while setting up secured application development practices: Security Training: The developers have to be given continuous training on application security. In this regard, OWASP Top 10 security related recommendations is of great help and a great place to start. This is primarily applicable for web applications. However, most of it also applies to general application. The security training is applicable for all stakeholders of the project including business analyst, project managers, architect, developers and testers. Threat Modeling: This is the most important aspect of all. This primarily consists of following important steps: Threat classification: Following are some of the key threats one can …

I found it very helpful. However the differences are not too understandable for me