Tag Archives: Application Security
My All-Time Web Application Security Favorites

Following are my all time favorites web pages I frequently visit for remaining up-to-date with web application security: https://www.owasp.org/ Website I frequently visit to check out videos, presentations, Books etc. http://bsimm.com/ Website about building security in maturity model http://www.webappsec.org/ Website representing Web Application Security Consortium that publishes technical information, contributed articles, security guidelines, and other useful documentation. Businesses, educational institutions, governments, application developers, security professionals, and software vendors all over the world utilize their materials to assist with the challenges presented by web application security. Books: List of web application security books you would want to keep handy Web Application Security Interview Questions: List of some interesting web security interesting …
Developers lack Application Security Skills. Do You Agree?

[adsenseyu2] In my experience, I have found that almost 95% of application developers lack application security skills and at times, tend to complete their journey without knowing much of the security technologies and related skills. Ask them if they wrote secured code, and almost in 90% of cases, they may say “don’t know” or say, “yes, wrote parameterized queries”. I talked to some of the developers at different experience levels and found some of the following as their answers: Use secured frameworks, so why bother?: Well, frameworks that are used for application development takes care of security aspects. So, we rely upon these frameworks for security concerns and not pay …
How to Address Application Security in Agile Scrum Teams?
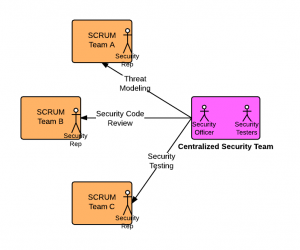
One of the concerns that takes the back burner while setting up the agile SCRUM teams is application security. One other area that gets similar behavior like security is performance which shall be addressed in later articles. However, performance gets addressed quickly as it is key quality characteristic and gets noticed by end users very quickly. In the traditional waterfall based development model, security gets fair attention as the non functional requirements related with security gets captured in the initial stages and the team gets composed of at least one security officer/specialist/architect to take care of security requirements. However, having a security specialist/officer in each SCRUM team is not feasible …
Minimum Security Coding to do Before Your Website Launch
I am sure you are very excited to launch your website as soon as the coding for minimum functionality is complete. However, I would only suggest some of the following as bare minimum which you may consider as important things to be taken care before your website launch: Input validation: Some of the following OWASP top 10 vulnerabilities can be averted if only we do coding for input validation. You would give an argument that you actually do the input validation and what different you need to do. All I would say is what you do in form of input validation is one or more of business rules representing boundary …
Top Security Considerations for your Cloud Applications
I have been working/reviewing a cloud application where data security has been shown as top security concerns for most of the customers. Following are key areas for consideration when planning for security for your cloud applications: Internal theft: One of the most crucial security thefts come from unscrupulous employees who can pass/leak data to the competitors. The customers using the cloud applications are suggested to advise their employees on this front. Physical access control & monitoring: The physical access to the data center hosting the cloud application should be restricted and monitored at all times. Login access control: Only authenticated users should be allowed to login.In addition, the authenticated users …
Key Considerations for Application Security & Agile SCRUM Team Composition
Before going into the SCRUM team composition in relation with application security, it can be worth while knowing what are key aspects of secured application development practices: Security awareness training Threat modeling Secured coding practices Secured code reviews Security testing Achieving the state of secured application development practices is one of the toughest challenges for most SCRUM MASTERS to crack. For achieving secured application development, different alternatives could be explored to build the team, depending on software development methodology including agile and non agile methodologies. For agile development based on SCRUM model, following alternatives can be explored: Security Officer/Adviser/Architect: The role of the security adviser is to counsel various SCRUM teams …
I found it very helpful. However the differences are not too understandable for me