OnePlus Store Website recently got discovered to be hacked as a result of which credit card details of more than 40,000 customers have been stolen.
In this post, you will learn about somee of the following:
- How the attack might have happened on/from OnePlus Checkout page?
- Who could be the hackers?
- How to prevent such attacks?
Malicious Code Injection may have resulted into Hack
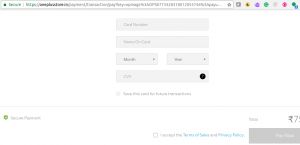
- Hacker might have hacked into the OnePlus website and injected malicious Javascript code in one of their javascript files which get loaded as a result of loading of checkout page. The following represent the screenshot of checkout page which is loaded from Onestore website. Look at the URL.
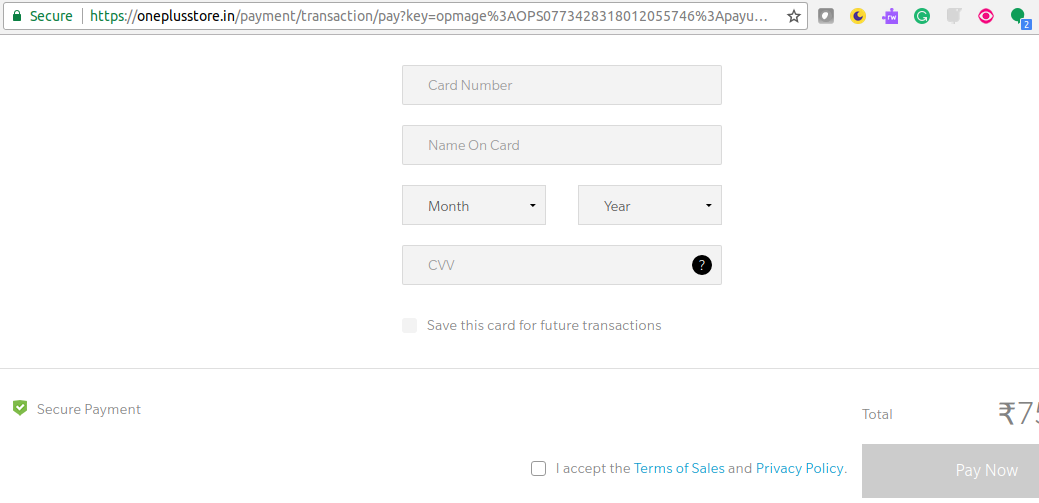
Figure 1. Oneplus Store Checkout Page
The checkout page gets loaded from the OneStore website as part of checkout process.
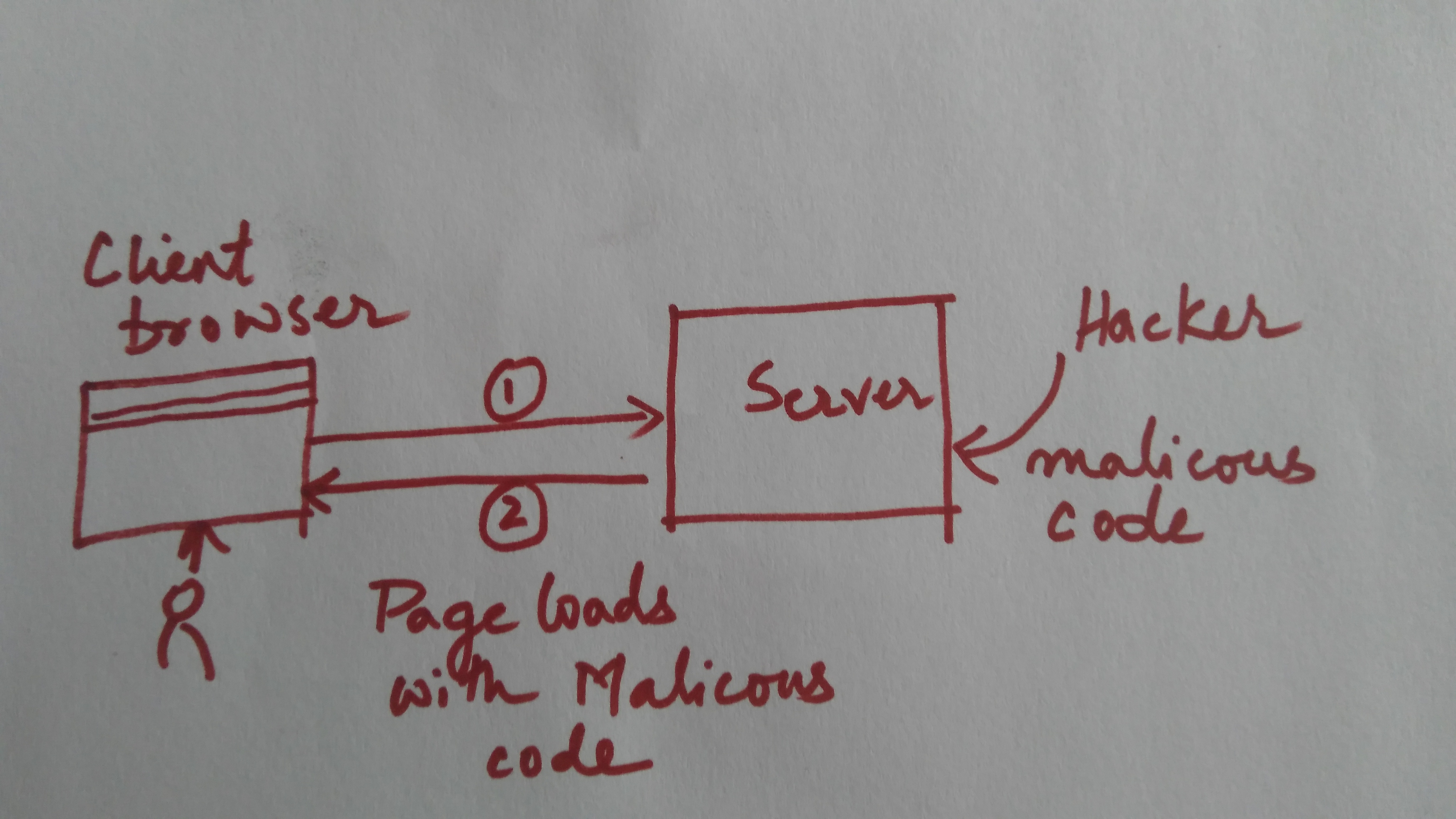
Figure 2. Checkout Page Loaded with Malicious Code
- Users enter the card details in checkout page and submit the form for payment. As a result of form submission, the malicious code would have sent the card details to the hacker server. The following diagram represents the same.
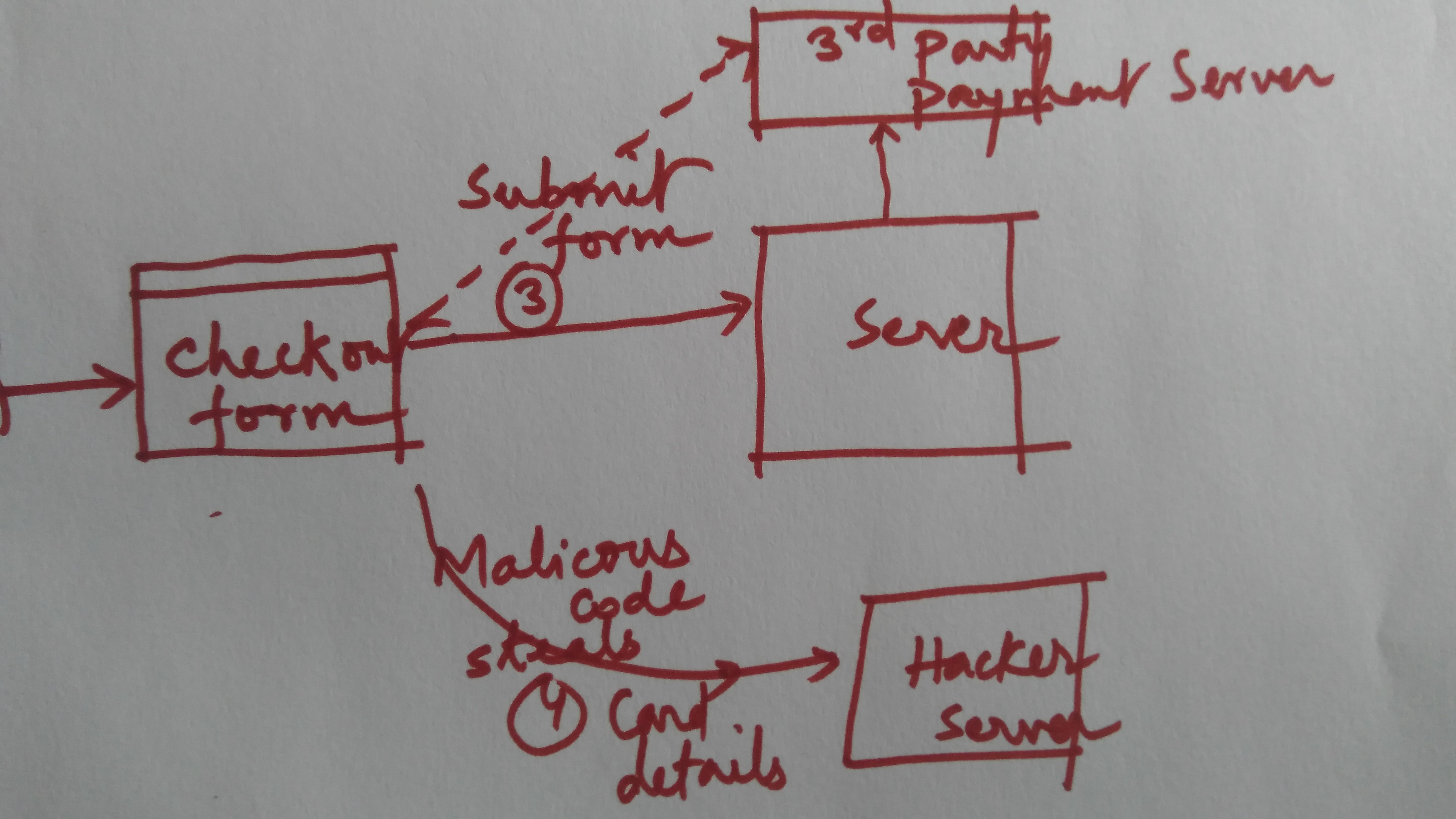
Figure 3. Credit Card Details being Stolen and sent to Hacker Server
The attack looks to be a case of Cross-site Scripting (XSS) attack in which malicious script/code is injected into the existing code which when loaded could capture the user data and pass them to hacker’s or attackers’ server.
Who could be the OnePlus Payment System Hackers?
Well, the following are different classes of hackers who could have led to malicious code injection:
- External hacker directly breaking into the webserver or hacking the webserver by some means and injecting the malicious code
- Someone from internal team (development team) could have turned into a hacker and injected the malicious code
- Someone from internal team would have injected the malicious code witht he help of external hacker
Lessons on how to Avoid such kind of Hacks/Attacks
As the malicious code might have got injected into existing JS files after hacker hacked into the server, the following are some of the ways in which such attack related to malicious code injection could be avoided:
- File integrity monitoring (FIM): FIM is a process of monitoring files and associated attributes to detect any changes made to the files. As part of file integrity monitoring, some of the following can be done to detect any code injection into existing files. This will prevent external or internal attacker to inject the code without being detected. It would be good to run one or more of the following checks at frequent intervals.
- File contents integrity monitoring (useful for configuration files)
- Files and folder access monitoring for protecting sensitive data
- Secure hash-based FIM for system files
- Code review process: Code review process would make sure that any changes to file will be reviewed by one or more persons. Thus, this would help prevent intentional or accidental code injection.
- Change control/monitoring process: Any changes to the critical/important files would need to be approved via the formal change management process thereby helping prevent intentional or accidental code injection.
- Background verification checks: As developers could do the malicious code injection, it would always help to make sure that developers’ background verification is done in order to detect any suspicious backgrounds of any sort.
Further Reading / References
Summary
In this post, you learnt about some of the following:
- What could have led to attack on OnePlus Payment System (Checkout)
- Who could be attackers in relation to malicious code injection?
- How to prevent such attacks?
Did you find this article useful? Do you have any questions about this article or suggestions regarding attack/hacking of OnePlus Payment system leading to credit card being stolen? Leave a comment and ask your questions and I shall do my best to address your queries.
- Coefficient of Variation in Regression Modelling: Example - November 9, 2025
- Chunking Strategies for RAG with Examples - November 2, 2025
- RAG Pipeline: 6 Steps for Creating Naive RAG App - November 1, 2025
I found it very helpful. However the differences are not too understandable for me