I was surfing a website, http://www.99acres.com, few days back and tried to retrieve my password using “Forgot Password” page. As I entered my username, I was amazed to see my email address shown there. I, then, tried another name such as “karthik” and following was the message:“An email has been sent to karthiksundaram@gmail.com. Please click on the link provided in the email to create a new password.”Take a look at the screenshot below as an evidence of the vulnerability.
Possible Exploit
As 99acres.com is one of the India’s largest retail website, one could easily write an automated script and retrieve email addresses of millions of users and then, use different techniques to retrieve few passwords as well.
Solution
The solution is pretty simple. The response message could look like following:
“An email has been sent to your registered email address. Please click on the link provided in the email to create a new password.”
[adsenseyu1]
- The Watermelon Effect: When Green Metrics Lie - January 25, 2026
- Coefficient of Variation in Regression Modelling: Example - November 9, 2025
- Chunking Strategies for RAG with Examples - November 2, 2025
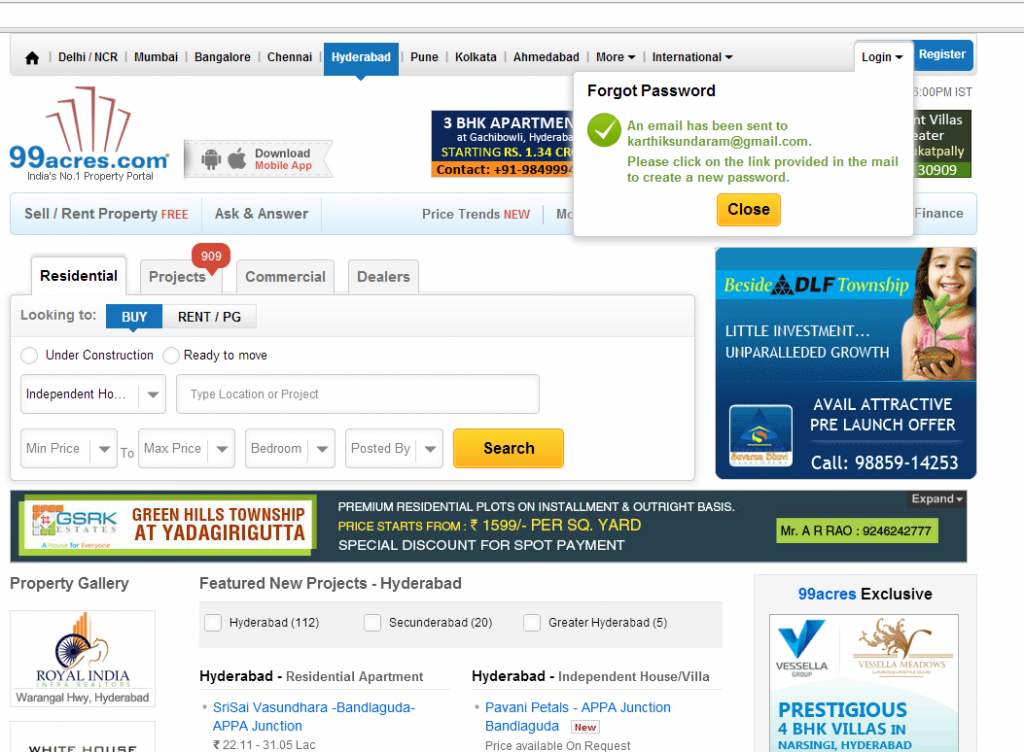

It was still broken as on 27.6.2014:17:52 – so dropped an updated to their website. Hope they can do anything better.
Interesting, but not necessarily “Broken Session” which happens when your session gets exposed, not some of your personal data. Lets say, in the “Forgot password” feature, you type your email and the app creates an authenticated session in this moment trying to prevent that you will not navigate to a private page, but for some reason, this prevention fails.